APSystems Altenergy Power Control
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability may allow remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of Altenergy Power Control software are affected: 3.2 VULNERABILITY OVERVIEW 3.2.1 IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN AN OS…
Schneider Electric EcoStruxure Products, Modicon PLCs, and Programmable Automation Controllers
Security Assessment of Schneider Electric Products Summary of Findings: During a security assessment of Schneider Electric’s EcoStruxure Products, Modicon PLCs, and Programmable Automation Controllers, several vulnerabilities were discovered. These vulnerabilities involve improper checks for unusual or exceptional conditions and could potentially lead to unauthorized access,…
Siemens SIMATIC Cloud Connect 7
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to execute arbitrary code. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following products from Siemens are affected: 3.2 VULNERABILITY OVERVIEW 3.2.1 IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN A COMMAND (‘COMMAND…
Hitachi Energy MSM
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to obtain user access credentials of the MSM web interface or cause a denial-of-service condition. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following Hitachi Energy products are affected: 3.2 VULNERABILITY…
Industrial Control Links ScadaFlex II SCADA Controllers
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an authenticated attacker to overwrite, delete, or create files. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of Industrial Control Links ScadaFlex II SCADA Controllers are affected: 3.2 VULNERABILITY OVERVIEW 3.2.1 EXTERNAL…
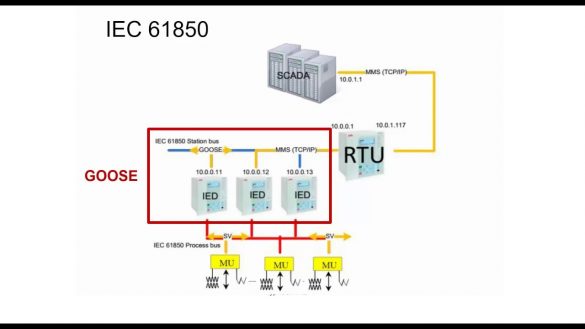
Hitachi Energy IEC 61850 MMS-Server
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could cause products using the IEC 61850 MMS-server communication stack to stop accepting new MMS-client connections. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions Hitachi Energy equipment using the IEC 61850 communication stack…
Security content of iOS 15.7.4 and iPadOS 15.7.4
About Apple security updates For our customers’ protection, Apple doesn’t disclose, discuss, or confirm security issues until an investigation has occurred and patches or releases are available. Recent releases are listed on the Apple security updates page. Apple security documents reference vulnerabilities by CVE-ID when possible. For more information…
Mitsubishi Electric MELSOFT iQ AppPortal
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Mitsubishi Electric Equipment: MELSOFT iQ AppPortal Vulnerabilities: HTTP Request Smuggling, Insufficient Verification of Data Authenticity 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow a malicious attacker to make unidentified impacts such as authentication bypass, information…
Johnson Controls System Configuration Tool (SCT)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely Vendor: Johnson Controls Equipment: System Configuration Tool Vulnerabilities: Sensitive Cookie Without ‘HttpOnly’ Flag, Sensitive Cookie in HTTPS Session Without ‘Secure’ Attribute 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to access cookies and take over the…
Mitsubishi Electric MELSEC iQ-R Series
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low attack complexity Vendor: Mitsubishi Electric Equipment: MELSEC iQ-R Series Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote unauthenticated attacker to cause a denial-of-service condition on a target product by sending specially crafted…








Stay connected