Exploit for Apple iOS version 12.1.3
Following our previous blog post “Analysis and Reproduction of iOS/OSX Vulnerability: CVE-2019-7286” we discussed the details of CVE-2019-7286 vulnerability – a double-free vulnerability that was patched in the previous release of iOS and was actively exploited in the wild. There is no public information about…
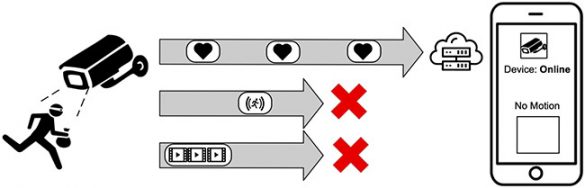
Flaws in the design of IoT devices prevent them from notifying homeowners about problems
esign flaws in smart home Internet of Things (IoT) devices that allow third parties to prevent devices from sharing information have been identified by researchers at North Carolina State University. On storage constrained IoT devices, the lack of buffering event notifications and content in embedded channels presents…
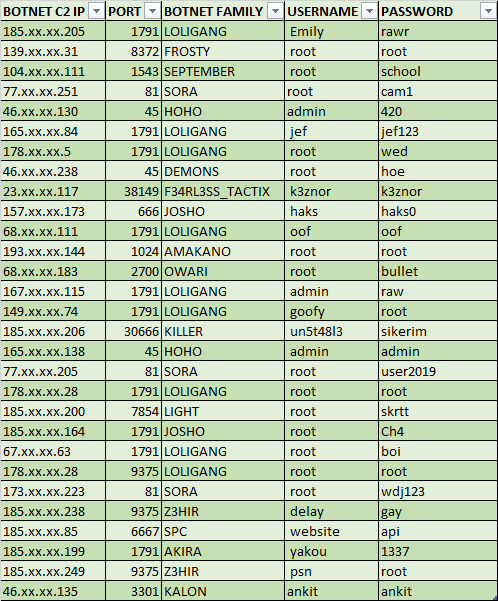
Several IoT botnet C2s compromised by a threat actor due to weak credentials
Introduction Most IoT botnets including Mirai and QBot count on getting access to the victim using weak/default credentials. However, a lot of times the threat actors themselves have poor opsec, with weak and default passwords in their command and control server. In theory, another black…
SCADA Shutdown Tool
Overview SCADAShutdownTool is industrial control system automation and testing tool allows security researchers and experts to test SCADA security systems, enumerate slave controllers, read controller’s registers values and rewrite registers data. SCADAShutdownTool allow enumeration of all registers types of a controller include coil outputs, digital…
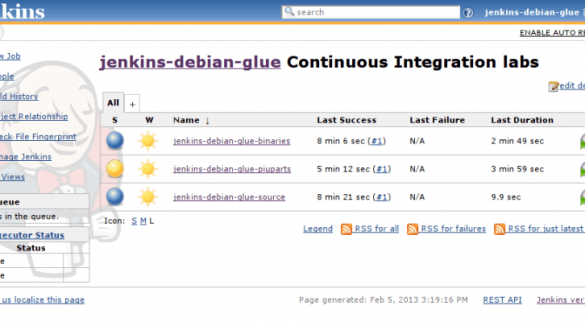
Vulnerabilities Found in Over 100 Jenkins Plugins
A researcher has discovered vulnerabilities in more than 100 plugins designed for the Jenkins open source software development automation server and many of them have yet to be patched. NCC Group Security Consultant Viktor Gazdag has manually tested hundreds of plugins that extend Jenkins’ functionality…
Sierra Wireless AirLink ALEOS
1. EXECUTIVE SUMMARY CVSS v3 9.1 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available Vendor: Sierra Wireless Equipment: AirLink ALEOS Vulnerabilities: OS Command Injection, Use of Hard-coded Credentials, Unrestricted Upload of File with Dangerous Type, Cross-site Scripting, Cross-site Request Forgery, Information Exposure, Missing Encryption of Sensitive Data…
GE Communicator
1. EXECUTIVE SUMMARY CVSS v3 8.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: General Electric Equipment: Communicator Vulnerabilities: Uncontrolled Search Path, Use of Hard-coded Credentials, Improper Access Controls 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to gain administrative privileges, manipulate widgets and UI…
Remote Code Execution on most Dell computers
What computer do you use? Who made it? Have you ever thought about what came with your computer? When we think of Remote Code Execution (RCE) vulnerabilities in mass, we might think of vulnerabilities in the operating system, but another attack vector to consider is…
Philips Tasy EMR
1. EXECUTIVE SUMMARY CVSS v3 4.1 ATTENTION: Low skill level to exploit Vendor: Philips Equipment: Tasy EMR Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could impact or compromise patient confidentiality and system integrity. Philips’ analysis has shown these issues, if fully exploited, may allow attackers…
Rockwell Automation CompactLogix 5370
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: CompactLogix 5370 Vulnerabilities: Uncontrolled Resource Consumption, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow a remote attacker to render the web server unavailable and/or place the controller…








Stay connected