Introduction
Just like every piece of software code, malware are not immune to vulnerabilities. In fact, most malware do not go through the process of Quality Control, and have more probability to have a bug. Sometimes these bugs can be (mis)used for various motives. In this blog, we will be discussing a trivial bug in Mirai code, which persists in many of its variants as well. Script kiddies and rival threat actors alike often use it to crash each others’ C2 servers.
Explaining the bug

When someone connects to a Mirai C2, it asks for a username and password to authenticate. If someone adds a stream of 1025+ characters in the username, the C2 crashes as shown above. Below we will discuss why this happens, first by explaining a simple program and then going to Mirai.
A badly written program
Given below is a program in GO which takes name as the input and prints it. The program first takes the name as a string, copies it in a byte buffer and then prints the buffer.While things may look normal at first, the program has a flaw. Notice that the buffer is declared statically of size 10.

Things go well when we run this and provide a small input, for example “Ankit”. However when we supply an input bigger than size 10, like “Ankitxxxxxxxxxxxxxxxxxxxx” then the program obviously throws an error.

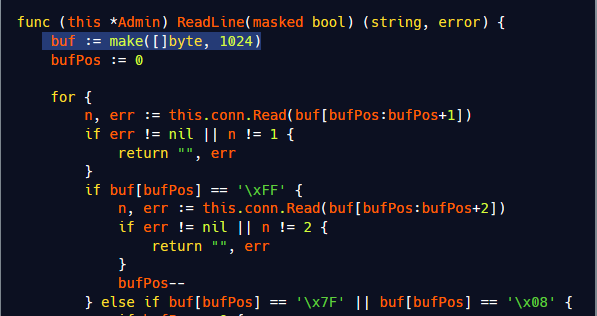
Going back to Mirai
Let’s go back to the original Mirai source now.

We see that the username is passed to the Readline function. While it may seem to be a library function due to its name, it is in fact a custom function declared in the source, which declares a fixed buffer size length of 1024. This is the reason why the module crashes when the username is a stream of 1025 or more characters.

Conclusion
Since a majority of IoT botnets even in 2019 are based of Mirai, this vulnerability has been passed out in many of the variants and is already used in full force among Blackhats. When we asked Scarface, an established IoT threat actor about it, he said “Yes,I have often used this to annoy script kiddies who sell botnet spots. The C2 stays down until the botnet owner realizes that the C2 is down and opens it again. I do think it is very relevant because if a script were to be made to check when the C2 is up and crash it continuously, it will make all Mirai based botnets pretty much useless.”
Do not try this at home
A lot of enthusiastic white hats want to make the world of CyberSecurity safer. Some may think its useful to create a daemon service which keeps on crashing all known C2 servers in a loop. However, such practice of crashing all these Mirai type C2 servers may not be permitted according to local laws, even if one is disrupting malicious servers. Hence the best way to stop a server is not to take matter in your own hands, but to report the IP to the hosting provider, CERT or law enforcement, which many white hats are already doing rigorously.
Source:
https://www.ankitanubhav.info/post/crash

Stay connected