Hitachi Energy MSM Product
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Hitachi Energy Equipment: MSM Product Vulnerability: Reliance on Uncontrolled Component 2. RISK EVALUATION Successful exploitation of this vulnerability could disrupt the functionality of the MSM web interface, steal sensitive user credentials, or cause a denial-of-service condition. 3….
Siemens Linux-based Products (Update J)
1. EXECUTIVE SUMMARY 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-21-131-03 Siemens Linux-based Products (Update I) that was published August 11, 2022, to the ICS webpage at www.cisa.gov/ics. 3. RISK EVALUATION Successful exploitation of this vulnerability could compromise…
Schneider Electric EcoStruxure, EcoStruxure Process Expert, SCADAPack RemoteConnect for x70
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Schneider Electric Equipment: EcoStruxure, EcoStruxure Process Expert, SCADAPack RemoteConnect for x70 Vulnerabilities: Heap-based Buffer Overflow, Wrap or Wraparound, Classic Buffer Overflow, Out-of-bounds Write 2. RISK EVALUATION The successful exploitation of these vulnerabilities on the affected products could…
Siemens Datalogics File Parsing Vulnerability (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low attack complexity Vendor: Siemens Equipment: Teamcenter Visualization and JT2Go Vulnerability: Heap-based buffer Overflow 2. UPDATE This updated advisory is a follow-up to the original advisory titled ICSA-22-195-07 Siemens Datalogics file Parsing Vulnerability that was published July 14, 2022, on the ICS…
Digi ConnectPort X2D
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low attack complexity Vendor: Digi International, Inc. Equipment: ConnectPort X2D Gateway Vulnerability: Execution with Unnecessary Privileges 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to execute malicious actions resulting in code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED…
Mitsubishi Electric GT SoftGOT2000
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Mitsubishi Electric Equipment: GT SoftGOT2000 Vulnerabilities: Infinite Loop, OS Command Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities could create a denial-of-service condition or enable arbitrary code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following…
Siemens Industrial Products with OPC UA (Update A)
1. EXECUTIVE SUMMARY CVSS v3 6.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: SIMATIC NET PC, SITOP Manager, TeleControl Server Basic Vulnerability: Null Pointer Dereference 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-22-132-08 Siemens Industrial Products with OPC UA that was…
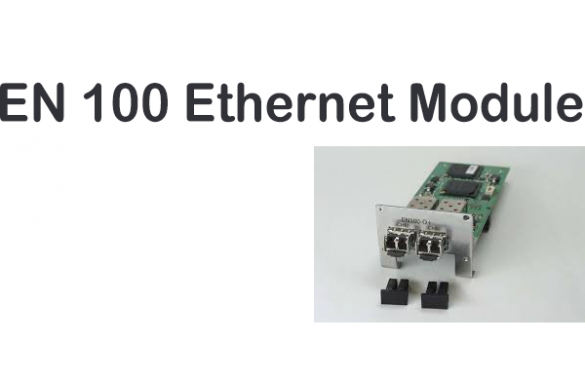
Siemens EN100 Ethernet Module
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: EN100 Ethernet Module Vulnerability: Improper Restriction of Operations within the Bounds of a Memory Buffer. 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to crash the affected application leading to a…
Siemens PADS Standard/Plus Viewer
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low attack complexity Vendor: Siemens Equipment: PADS Standard/Plus Viewer Vulnerabilities: Out-of-bounds Read, Out-of-bounds Write, Improper Restriction of Operations within the Bounds of a Memory Buffer 2. RISK EVALUATION Successful exploitations of these vulnerabilities could allow an attacker to trick a user into…
Siemens EN100 Ethernet Module
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: EN100 Ethernet Module Vulnerability: Improper Restriction of Operations within the Bounds of a Memory Buffer 2. RISK EVALUATION Successful exploitation of this vulnerability could lead to the product crashing or the creation of a denial-of-service…








Stay connected