Mitsubishi Electric MELSEC iQ-F FX5-OPC
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote attacker to cause a Denial-of-Service (DoS) condition on the product by getting a legitimate user to import a specially crafted PKCS#12 format certificate. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The…
Cisco Catalyst SD-WAN Routers Denial of Service Vulnerability
Summary A vulnerability in the process that classifies traffic that is going to the Unified Threat Defense (UTD) component of Cisco IOS XE Software in controller mode could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on an affected device….
DragonForce Ransomware Expands RaaS, Targets Firms Worldwide
DragonForce ransomware is expanding its RaaS operation and becoming a global cybersecurity threat against businesses. Companies must implement strong cybersecurity strategies to defend against this growing ransomware attack and avoid becoming victims. Ransomware attacks are growing, leaving organizations vulnerable to new and more sophisticated threats. According…
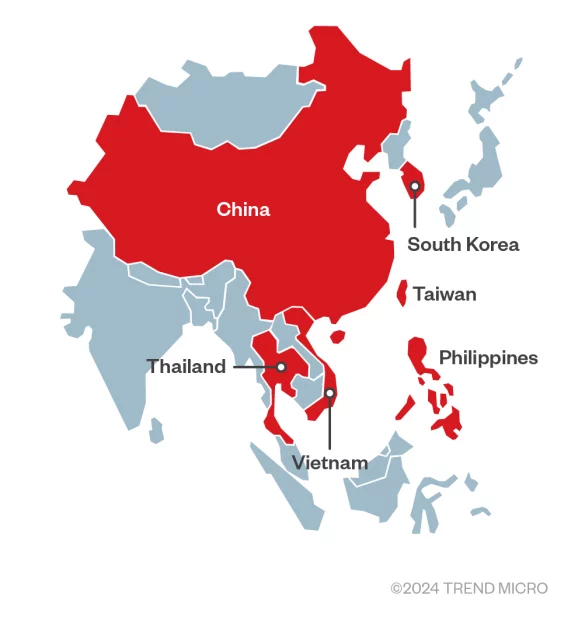
Chinese APT Earth Baxia target APAC by exploiting GeoServer flaw
Suspected China-linked APT Earth Baxia targeted a government organization in Taiwan by exploiting a recently patched OSGeo GeoServer GeoTools flaw. Trend Micro researchers reported that China-linked APT group Earth Baxia has targeted a government organization in Taiwan and potentially other countries in the Asia-Pacific (APAC)…
IDEC CORPORATION WindLDR and WindO/I-NV4
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to obtain sensitive information. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of WindLDR and WindO/I-NV4 are affected: 3.2 Vulnerability Overview 3.2.1 CLEARTEXT STORAGE OF SENSITIVE INFORMATION CWE-312 The affected…
Rockwell Automation RSLogix 5 and RSLogix 500
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to perform remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of Rockwell Automation RSLogix 5 and RSLogix 500, a programming software, are affected: 3.2 Vulnerability Overview…
Hackers claim to have breached Israeli nuclear facility’s computer network
An Iran-linked hacking group claims to have breached the computer network of a sensitive Israeli nuclear installation in an incident declared by the ‘Anonymous’ hackers as a protest against the war in Gaza. The hackers claim to have stolen and published thousands of documents —…
Viessmann Climate Solutions SE Vitogate 300
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to achieve remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of Viessmann Climate Solutions SE Vitogate 300, a solution to connecting boilers and heat pumps to…
Cisco Smart Licensing Utility Vulnerabilities
Summary Multiple vulnerabilities in Cisco Smart Licensing Utility could allow an unauthenticated, remote attacker to collect sensitive information or administer Cisco Smart Licensing Utility services on a system while the software is running. Cisco has released software updates that address these vulnerabilities. There are no…
AVEVA Historian Web Server
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an authenticated user to get read and write access to the database. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of AVEVA Historian Server, a Process database, are affected: 3.2 Vulnerability…









Stay connected