A Windows zero-day flaw addressed by Microsoft with its latest Patch Tuesday updates is exploited by an APT group in attacks aimed at entities in the Middle East.
The Windows zero-day vulnerability tracked as CVE-2018-8453 is a privilege escalation flaw that was exploited by an APT group in attacks against entities in the Middle East.
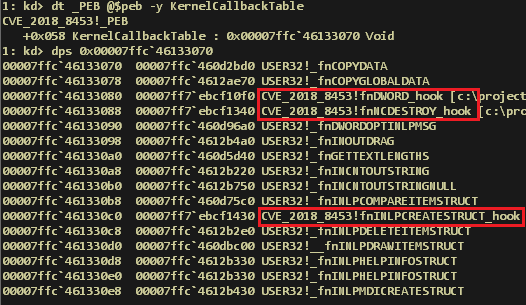
The flaw, tracked as CVE-2018-8453, affects the Win32k component of Windows handles objects in memory.
The flaw was discovered by experts from Kaspersky Lab could be exploited by an authenticated attacker to take control of an affected system.
Kaspersky Lab reported the vulnerability to Microsoft on August 17, roughly two months ago.
Kaspersky revealed that the CVE-2018-8453 vulnerability has been exploited by the APT group tracked as FruityArmor, a cyber-espionage group that was first observed in 2016 while targeting activists, researchers, and individuals related to government organizations.
Experts believe FruityArmor´s activity has been slowly increasing during the last two years.
The zero-day exploit was included by malware installer used by the group to escalate privileges on the target machine and to gain persistence.
The final payload dropped by the malware was a sophisticated implant used by the attackers for persistent access to the victims’ machines.”
“In August 2018 our Automatic Exploit Prevention (AEP) systems detected an attempt to exploit a vulnerability in Microsoft Windows operating system. Further analysis into this case led us to uncover a zero-day vulnerability in win32k.sys.” reads the report published by Kaspersky.
“The exploit was executed by the first stage of a malware installer to get necessary privileges for persistence on the victim’s system. The code of the exploit is of high quality and written with the aim of reliably exploiting as many different MS Windows builds as possible, including MS Windows 10 RS4.”
The zero-day resembles an older vulnerability tracked as CVE-2017-0263 that was fixed by Microsoft in May 2017 and that it had been exploited by the Russia-linked cyberespionage group tracked as APT28.
The zero-day exploit was used in targeted attacks against less than a dozen entities located in the Middle East.
“So far, this campaign has been extremely targeted, affecting a very low number of victims in the Middle East region, probably persons of interest for the attackers. However, the victimology is not clear, especially with such a small number of victims involved.” continues the report.
The attribution was possible due to the detection of a PowerShell backdoor that has previously been exclusively used by the FruityArmor APT. Experts also confirmed an overlap in the C2 infrastructure between the last campaign and previous attacks attributed to the group.
Source:
https://securityaffairs.co/wordpress/77003/apt/cve-2018-8453-win-0day.html