Experts discovered a flaw dubbed NetCAT (Network Cache ATtack) that affects all Intel server-grade processors and allows to sniff sensitive data over the network.
Researchers from VUSec group at Vrije Universiteit Amsterdam have discovered a new vulnerability that can be exploited by a remote attacker to sniff sensitive details by mounting a side-channel attack over the network.
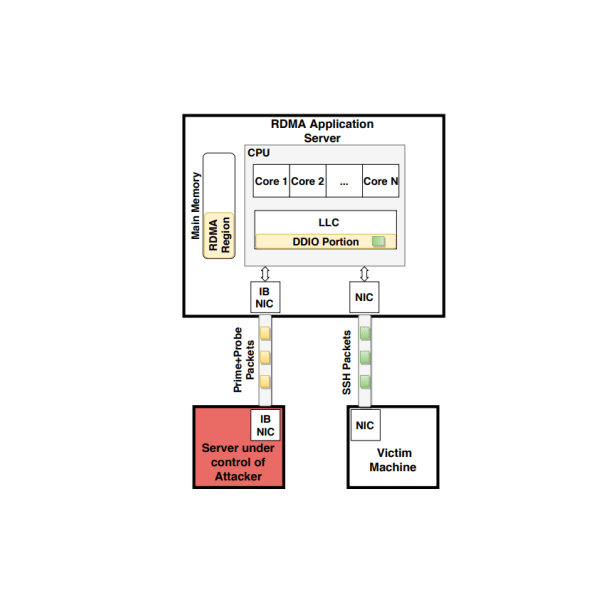
The weakness, tracked as CVE-2019-11184, resides in a performance optimization feature called Intel’s DDIO (Data-Direct I/O) that was implemented to grant network devices and other peripherals access to the CPU cache.
“With NetCAT, we show this threat extends to untrusted clients over the network, which can now leak sensitive data such as keystrokes in a SSH session from remote servers with no local access.” reads the analysis published by the researchers. “The root cause of the vulnerability is a recent Intel feature called DDIO, which grants network devices and other peripherals access to the CPU cache.”
An attacker controlling a machine on the target network can exploit the flaw to infer confidential data from an SSH session.
The experts explained that using a machine learning algorithm against the time information it is possible to perform a keystroke timing analysis to discover the words typed by a victim.
“In an interactive SSH session, every time you press a key, network packets are being directly transmitted. As a result, every time a victim you type a character inside an encrypted SSH session on your console, NetCAT can leak the timing of the event by leaking the arrival time of the corresponding network packet,” continues the experts.
“Now, humans have distinct typing patterns. For example, typing’s’ right after ‘a’ is faster than typing ‘g’ after’s.’ As a result, NetCAT can operate statical analysis of the inter-arrival timings of packets in what is known as a keystroke timing attack to leak what you type in your private SSH session.”
The researchers discovered that compared to a native local attacker, the NetCAT attack conducted by a remote attacker only reduces the accuracy of the discovered keystrokes on average by 11.7% by discovering inter-arrival of SSH packets with a true positive rate of 85%.
The following demo video published by the researchers shows how
spying on SSH sessions in real-time leveraging a shared server.
Intel recommends users to either disable DDIO or at least RDMA to make it hard to carry out this attack. The chip vendor also suggested limiting direct access to the servers from untrusted networks.
Intel classified NetCAT as a partial information disclosure issue with “low” (CVSS base score of 2.6). Intel awarded VUSec experts for the responsible disclosure.
Technical details of the research are reported in a paper published by the experts and titled “NetCAT: Practical Cache Attacks from the Network.”
Source:
https://www.us-cert.gov/ics/advisories/icsa-19-248-01