Introduction
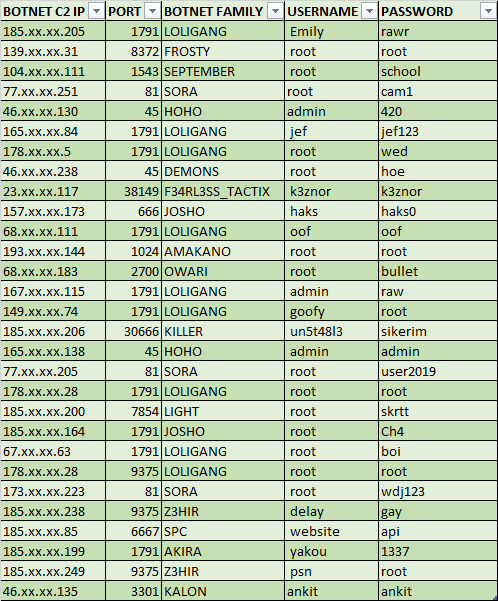
Most IoT botnets including Mirai and QBot count on getting access to the victim using weak/default credentials. However, a lot of times the threat actors themselves have poor opsec, with weak and default passwords in their command and control server. In theory, another black hat can simply launch a brute force attack on these C2 servers and get access to bots without even running their own botnet. Now this theory has been implemented by a threat actor named Subby, who has brute forced at least 29 IoT C2s, and found them using extremely trivial credentials. As shared by the threat actor, one can see that the credentials used are fairly weak.
Interview with the threat actor Subby
I decided to ping Subby to know more answers besides the data, like why and how he is doing this, and what is the motive. Some of the excerpts from the interview are as follows:
Ankit – What technique you are using for brute forcing the servers?
Subby – I have a network of honeypots configured to capture binaries over Telnet/SSH. The captured C2 IPs are then port scanned via NMAP to find the C2 port. For brute forcing, I am using a dictionary style attack coupled with a password list which has common user: pass combo’s. In addition to this ,each C2 undergoes a random style password attack which continues up to 6 alphanumeric characters under the user ‘root’. I change the user to something specific if I have prior knowledge of the C2. Each cracked password is added to the password list used when brute forcing the C2s in future.
Ankit – As you have found out, many of the credentials are very weak. Why you think this is happening?
Subby – It’s obvious as to why this is happening. A large percentage of botnet operators are simply following tutorials which have spread around in the community or are accessible on YouTube to set up their botnet. When following these tutorials, they do not change the default credentials. If they do change the credentials the password they supply is generally weak and therefore vulnerable to brute forcing.
Ankit – How much total bot count you have achieved brute forcing these c2?
Subby – Within the 1st week of brute forcing, I surpassed 40,000 devices. This was quite an inflated number due to possible duplication. It is well documented that botnet operators like to artificially increase their bot count. I estimate the number to be closer to 25,000 unique devices. I was able to get a reliable network traffic graph produced of the traffic generated from all the botnets combined and it was just under 300gbit/s. This high number was achieved because of the vast amount of Digital Ocean servers on many of the botnets. It is well known that Digital Ocean are relatively slow in comparison to other hosts when dealing with abuse complaints. Since then, the number of C2’s vulnerable to brute forcing has lowered considerably, (30-40%).This is likely due to how vocal I’ve been when brute forcing the servers, I have actively contacted botnet operators letting them know that I managed to obtain access to their C2.
Ankit – Why are you doing this? Are you using this for DDoS?
Subby – The main reason I undertook this task initially was to see how well brute forcing would work on C2 servers and whether it would be an efficient way of getting access to devices ,rather than having to use exploits or the usual loading onto devices with weak passwords via Telnet/SSH. Since Mirai was released ,Telnet has slowly become saturated and it’s hard to get a decent number of bots. I have only used the C2s to attack network traffic graphs which are setup to be attacked to analyze inbound traffic.
Conclusion
In one previous case, we observed the SQL database of an IoT botnet having root:root credentials before, but as we see now, the problem is bigger and not a one-off case. Pure novices in the field of IoT are increasing. We are not talking about script kiddies, but such low skilled actors who are unable to set up a botnet from source, yet they want to launch a DDoS by doing nothing other than pressing a button. We also observed mistakes as novice as not replacing the botnet dummy C2 IP with their own IP.
Unstable(UN5T48L3), the Turkey based author of Z3hir IoT botnet has gone to the extent to release a video where he tells how to replace the dummy C2 (0.0.0.0) with the attacker’s IP. When asked about the video, he told “Yes, these script kiddies are not changing IPs and they are blaming me when the botnet does not work“. Recently @VessonSecurity also observed a similar case where his honeypots found attacks with dummy C2 “INSERT-IP-HERE-N*GGA”, pointing to the fact that the threat actor forgot to change the dummy C2 with a real one, yet proceeded to attack the IoT devices (and subsequently the honeypots) with a non functioning C2.
Interestingly, despite not knowing what they are doing, the script kiddies often succeed, thanks to good support and tutorial videos by threat actors. In many cases like having a secure password and updating the IoT device can save one from these low hanging fruit attacks.
Source:
https://www.ankitanubhav.info/post/c2bruting