CheckPoint firm uncovered a cyber espionage campaign leveraging a weaponized version of TeamViewer to target officials in several embassies in Europe.
Security experts at CheckPoint uncovered a cyber espionage campaign leveraging a weaponizedversion of TeamViewer and malware disguised as a top-secret US government document to target officials in several embassies in Europe.
The targeted attacks aimed at Embassy officials from at least seven countries (Italy, Kenya, Bermuda, Nepal, Guyana, Lebanon, and Liberia), individuals hit by the hackers were tied to government revenue related roles and the financial sector. This aspect suggests a possible financial motivation for the campaign.
The nature of the targets and the multiple-stage nature of the attacks suggest the involvement of a nation state attacker.
According to the experts, the malicious code and the decoy documents were developed by an individual that goes online with the handle EvaPiks.
EvaPiks was also the moniker of a user of an illegal Russian-carding forum for some time.
“Although in such campaigns it is usually unclear who is behind the attack, in this case we were able to locate a user who appears to be behind the aforementioned activity active in several online forums, or is at least the creator of the tools used in the attack.” reads the analysis published by CheckPoint.
“By following the trail from the previous campaigns we were able to find a `CyberForum[.]ru` user that goes by the name “EvaPiks”In multiple instances, the user would suggest, or be advised by other users to use, some of the techniques we witnessed throughout the campaigns.”
EvaPiks is suspected to be the developer of the entire infection chain.
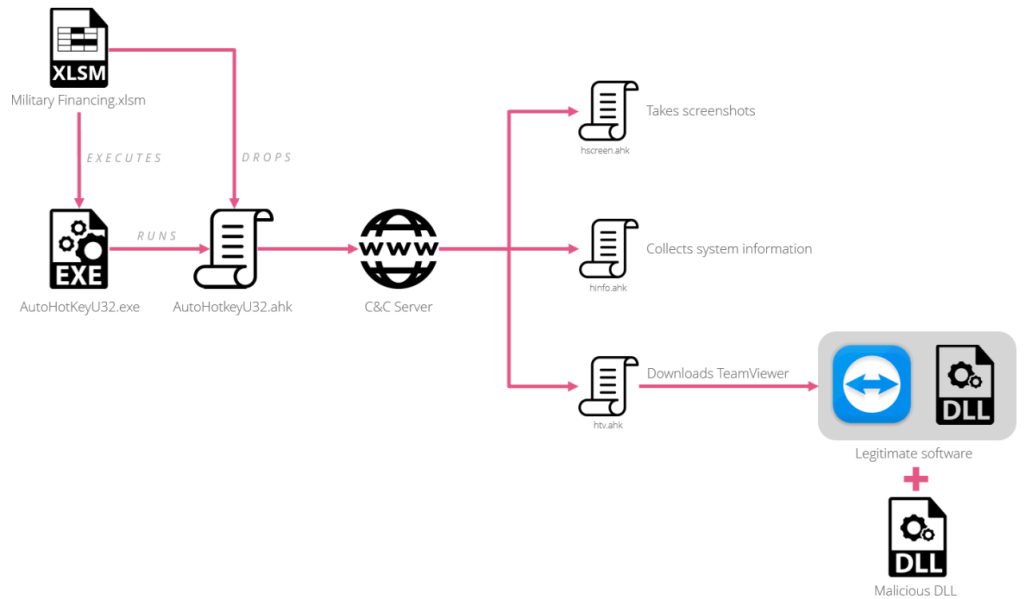
The attack chain starts with spear-phishing messages using an XLSM document with malicious macros and having as a subject “Military Financing Program.”
The decoy document is well-crafted, it shows a logo of the US Department of State on it and marked as top secret.
“Although the attackers have worked hard to make the document appear convincing, they seem to have overlooked some Cyrillic artifacts (such as the Workbook name) that were left in the document, and could potentially reveal more information about the source of this attack.” continues the analysis.
The macros extract the following files from encoded cells within the XLSM document:
- a legitimate AutoHotkey (AHK) program;
- a malicious version of AHK that connects to a C2 server to fetch and execute a Trojanized version of TeamViewer that establish a backdoor in the infected system.
The malicious TeamViewer can also include other features such as hiding the interface of TeamViewer, saving the current TeamViewer session credentials to a text file, allowing the transfer and execution of additional EXE or DLL files.
Experts pointed out that EvaPiks has been involved in previous campaigns where attackers used other weaponized versions of TeamViewer.
One of the variants analyzed by Check Point implemented had the ability to send some basic system information back to the attacker and to delete itself from the infected system. A second variant observed in 2018 used a new command system and targeted a long list of banks, cryptocurrency exchange, and e-commerce sites.
The third and current variant implements a DLL execution feature and uses external AutoHotKey scripts to gather information and session credentials.
“On the one hand, from the findings we have described, this appears to be a well thought-out attack that carefully selects a handful of victims and uses tailored decoy content to match the interests of its target audience.
On the other hand, some aspects of this attack were carried out with less caution, and have exposed details that are usually well disguised in similar campaigns, such as the personal information and online history of the perpetrator, as well as the outreach of their malicious activity.” concludes CheckPoint.
“However, the activity history of the developer behind the attack in underground carding forums and the victim’s characteristics may imply that the attacker is financially motivated.”
Further technical details, including IoCs are reported in the analysis published by the experts.
Source:
https://securityaffairs.co/wordpress/84367/hacking/trojanized-teamviewer-hit-embassies.html