Publicly Available Tools Seen in Cyber Incidents Worldwide
Summary This report is a collaborative research effort by the cyber security authorities of five nations: Australia, Canada, New Zealand, the United Kingdom, and the United States.[1][2][3][4][5] In it we highlight the use of five publicly available tools, which have been used for malicious purposes…
Siemens SCALANCE W1750D
1. EXECUTIVE SUMMARY CVSS v3 5.9 ATTENTION: Exploitable remotely/public exploits are available Vendor: Siemens Equipment: SCALANCE W1750D Vulnerability: Cryptographic issues 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to decrypt TLS traffic. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Siemens reports the vulnerability affects the following…
Siemens ROX II
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: ROX II Vulnerabilities: Improper Privilege Management 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow valid users to escalate their privileges and execute arbitrary commands. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Siemens…
Siemens SIMATIC S7-1200 CPU Family Version 4
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely Vendor: Siemens Equipment: SIMATIC S7-1200 CPU Family Version 4 Vulnerability: Cross-Site Request Forgery (CSRF) 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a CSRF attack if an unsuspecting user is tricked into accessing a malicious link. 3. TECHNICAL…
Siemens SIMATIC S7-1500, SIMATIC S7-1500 Software Controller and SIMATIC ET 200SP Open Controller
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC S7-1500, SIMATIC S7-1500 Software Controller and SIMATIC ET 200SP Open Controller Vulnerability: Denial of Service from improper input validation 2. RISK EVALUATION An attacker with network access to the PLC may be…
Hangzhou Xiongmai Technology Co., Ltd XMeye P2P Cloud Server
1. EXECUTIVE SUMMARY CVSS v3 8.1 ATTENTION: Exploitable remotely/low skill level to exploit/information related to these vulnerabilities is publicly available Vendor: Hangzhou Xiongmai Technology Co., Ltd Equipment: XMeye P2P Cloud Server Vulnerabilities: Predictable From Observable State, Hidden Functionality, Missing Encryption of Sensitive Data 2. RISK EVALUATION Successful exploitation of…
Fuji Electric Energy Savings Estimator
1. EXECUTIVE SUMMARY CVSS v3 7.3 Vendor: Fuji Electric Equipment: Fuji Electric Energy Savings Estimator Vulnerability: Uncontrolled Search Path Element 2. RISK EVALUATION Successful exploitation of this vulnerability may allow an attacker to load a malicious DLL and execute code on the affected system with the same privileges…
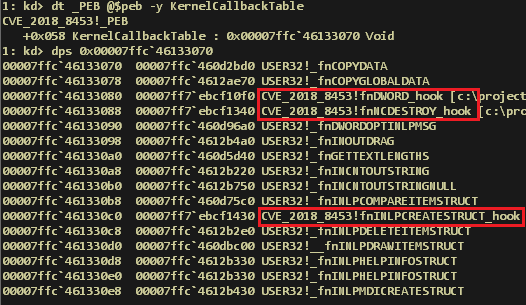
CVE-2018-8453 Zero-Day flaw exploited by FruityArmor APT in attacks aimed at Middle East
A Windows zero-day flaw addressed by Microsoft with its latest Patch Tuesday updates is exploited by an APT group in attacks aimed at entities in the Middle East. The Windows zero-day vulnerability tracked as CVE-2018-8453 is a privilege escalation flaw that was exploited by an APT group in attacks…
Siemens OpenSSL Vulnerability in Industrial Products
1. EXECUTIVE SUMMARY CVSS v3 5.9 ATTENTION: Exploitable remotely Vendor: Siemens Equipment: Industrial Products Vulnerability: Cleartext Transmission of Sensitive Information 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-18-226-02 Siemens OpenSSL Vulnerability in Industrial Products (Update A) that was…
Siemens SIMATIC STEP 7 and SIMATIC WinCC (Update A)
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable locally/low skill level to exploit Vendor: Siemens Equipment: SIMATIC STEP 7 (TIA Portal) and SIMATIC WinCC (TIA Portal) Vulnerabilities: Incorrect Default Permissions 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-18-226-01 Siemens SIMATIC STEP 7…








Stay connected