New Malware Combines Ransomware, Coin Mining and Botnet Features in One
Windows and Linux users need to beware, as an all-in-one, destructive malware strain has been discovered in the wild that features multiple malware capabilities including ransomware, cryptocurrency miner, botnet, and self-propagating worm targeting Linux and Windows systems. Dubbed XBash, the new malware, believed to be…
Hackers Steal Customers’ Credit Cards From Newegg Electronics Retailer
The notorious hacking group behind the Ticketmaster and British Airways data breaches has now victimized popular computer hardware and consumer electronics retailer Newegg. Magecart hacking group managed to infiltrate the Newegg website and steal the credit card details of all customers who entered their payment card information between August 14 and September…
Zero-Day Bug Allows Hackers to Access CCTV Surveillance Cameras
Firmware used in up to 800,000 CCTV cameras open to attack thanks to buffer overflow zero-day bug. Between 180,000 and 800,000 IP-based closed-circuit television cameras are vulnerable to a zero-day vulnerability that allows hackers to access surveillance cameras, spy on and manipulate video feeds or…
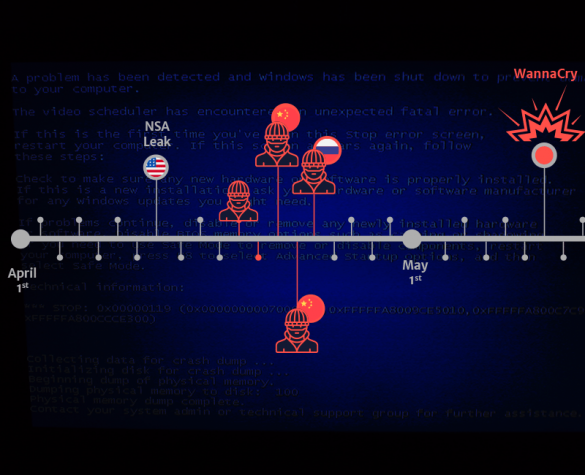
Cracked Windows installations are serially infected with EternalBlue exploit code
According to Avira, hundreds of thousands of unpatched Windows systems are serially infected with EternalBlue exploit code. The EternalBlue, is the alleged NSA exploit that made the headlines with DOUBLEPULSAR in the WannaCry attack. The malicious code was leaked online by the Shadow Brokers hacking group that stole it from the arsenal of the…
EOSBet Gambling application hacked, crooks stole $200,000 worth of EOS
The gambling application EOSBet was affected by a vulnerability in its smart contract system that has been exploited by attackers to steal $200,000 worth of EOS. The security breach was first reported by the member “thbourlove” of the EOSBet Reddit community that shared the code used to exploit the flaw. After…
Ransomware Attack Takes Down Bristol Airport’s Flight Display Screens
Bristol Airport has blamed a ransomware attack for causing a blackout of flight information screens for two days over the weekend. The airport said that the attack started Friday morning, taking out several computers over the airport network, including its in-house display screens which provide…
Flaw in update process for BMCs in Supermicro servers allows to deliver persistent malware or brick the server
A team of security researchers discovered a vulnerability in the baseboard management controller (BMC) hardware used by Supermicro servers. Researchers from security firm Eclypsium have discovered a vulnerability in the firmware update mechanism that could be exploited by hackers to deliver persistent malware, completely wipe and reinstall…
BusyGasper spyware remained undetected for two years while spying Russians
Security experts from Kaspersky Lab have uncovered a new strain of Android malware dubbed BusyGasper that remained hidden for two years. The BusyGasper Android spyware has been active since May 2016, it implements unusual features for this type of malware. Experts explained it is a unique…
Philips e-Alert Unit
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit/exploitable from within the same local subnet Vendor: Philips Equipment: Philips e-Alert Unit (non-medical device) Vulnerabilities: Improper Input Validation, Cross-site Scripting, Information Exposure, Incorrect Default Permissions, Cleartext Transmission of Sensitive Information, Cross-site Request Forgery, Session Fixation, Resource…
Martem TELEM-GW6/GWM (Update B)
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Martem Equipment: TELEM-GW6/GWM ——— Begin Update B Part 1 of 5 ——– Vulnerabilities: Missing Authentication for Critical Function, Incorrect Default Permissions, Resource Exhaustion, Cross-Site Scripting ——— End Update B Part 1…







Stay connected