WAGO M&M Software fdtCONTAINER (Update C)
1. EXECUTIVE SUMMARY CVSS v3 7.3 ATTENTION: Low skill level to exploit Vendor: M&M Software GmbH, a subsidiary of WAGO Kontakttechnik Equipment: fdtCONTAINER Vulnerability: Deserialization of Untrusted Data 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-21-021-05 WAGO M&M Software fdtCONTAINER (Update B)…
Rockwell Automation ISaGRAF5 Runtime (Update A)
1. EXECUTIVE SUMMARY CVSS v3 9.1 ATTENTION: Exploitable remotely/low attack complexity Vendor: Rockwell Automation Equipment: ISaGRAF5 Runtime Vulnerabilities: Use of Hard-coded Cryptographic Key, Unprotected Storage of Credentials, Relative Path Traversal, Uncontrolled Search Path Element, Cleartext Transmission of Sensitive Information\ 2. UPDATE INFORMATION This updated advisory is a follow-up to the…
ThroughTek P2P SDK
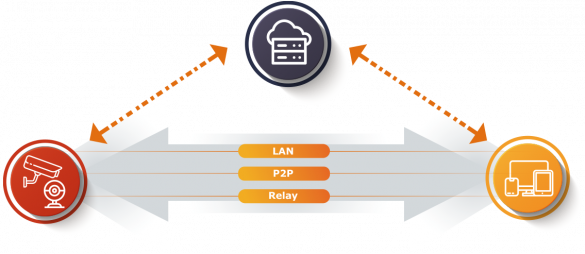
1. EXECUTIVE SUMMARY CVSS v3 9.1 ATTENTION: Exploitable remotely/low attack complexity Vendor: ThroughTek Equipment: P2P SDK Vulnerability: Cleartext Transmission of Sensitive Information 2. RISK EVALUATION ThroughTek supplies multiple original equipment manufacturers of IP cameras with P2P connections as part of its cloud platform. Successful exploitation of this vulnerability could…
Automation Direct CLICK PLC CPU Modules
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Automation Direct Equipment: CLICK PLC CPU modules Vulnerabilities: Authentication Bypass Using an Alternate Path or Channel, Cleartext Transmission of Sensitive Information, Unprotected Storage of Credentials 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker…
OpenClinic GA (Update B)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available Vendor: OpenClinic GA is a product of open-source collaboration on Source Forge Equipment: OpenClinic GA Vulnerabilities: Authentication Bypass Using an Alternate Path or Channel, Improper Restriction of Excessive Authentication Attempts, Improper Authentication, Missing…
ZOLL Defibrillator Dashboard
1. EXECUTIVE SUMMARY CVSS v3 9.9 ATTENTION: Exploitable remotely/low attack complexity Vendor: ZOLL Equipment: Defibrillator Dashboard Vulnerabilities: Unrestricted Upload of File with Dangerous Type, Use of Hard-coded Cryptographic Key, Cleartext Storage of Sensitive Information, Cross-site Scripting, Storing Passwords in a Recoverable Format, Improper Privilege Management 2. RISK EVALUATION Successful…
Rockwell Automation FactoryTalk Services Platform
1. EXECUTIVE SUMMARY CVSS v3 8.5 ATTENTION: Exploitable remotely Vendor: Rockwell Automation Equipment: FactoryTalk Services Platform Vulnerability: Protection Mechanism Failure 2. RISK EVALUATION Successful exploitation of this vulnerability may allow remote, authenticated users to bypass FactoryTalk Security policies that are based on a computer name. 3. TECHNICAL DETAILS 3.1…
AGG Software Web Server Plugin
1. EXECUTIVE SUMMARY CVSS v3 8.2 ATTENTION: Exploitable remotely/low attack complexity Vendor: AGG Software Equipment: Web Server Vulnerabilities: Path Traversal, Cross-site Scripting 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow remote code execution and exposure of arbitrary system files. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following…
Advantech iView
1. EXECUTIVE SUMMARY CVSS v3 9.1 ATTENTION: Exploitable remotely/low attack complexity Vendor: Advantech Equipment: iView Vulnerabilities: Missing Authentication for Critical Function, SQL Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to disclose information and perform remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS…
Hillrom Medical Device Management
1. EXECUTIVE SUMMARY CVSS v3 5.9 ATTENTION: Exploitable remotely Vendor: Hillrom Equipment: Welch Allyn medical device management tools Vulnerabilities: Out-of-Bounds Write, Out-of-Bounds Read 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to cause memory corruption and remotely execute arbitrary code. 3. TECHNICAL DETAILS 3.1 AFFECTED…










Stay connected