Siemens Industrial Products (Update G)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Industrial Products ——— Begin Update G Part 1 of 4 ——— Vulnerabilities: Excessive Data Query Operations in a Large Data Table, Integer Overflow or Wraparound, Uncontrolled Resource Consumption ——— End Update G…
Siemens SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM (Update H)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM Vulnerability: Out-of-bounds Read 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-19-099-06 Siemens SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM (Update G)…
Medtronic Conexus Radio Frequency Telemetry Protocol (Update B)
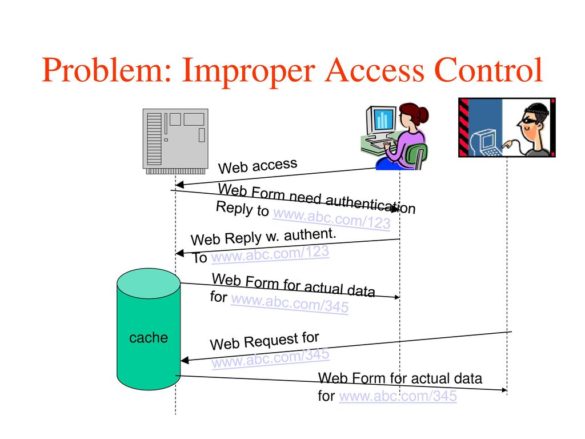
1. EXECUTIVE SUMMARY CVSS v3 9.3 ATTENTION: Exploitable with adjacent access/low skill level to exploit Vendor: Medtronic Equipment: MyCareLink Monitor, CareLink Monitor, CareLink 2090 Programmer, specific Medtronic implanted cardiac devices listed below Vulnerabilities: Improper Access Control, Cleartext Transmission of Sensitive Information 2. UPDATE INFORMATION This updated advisory is a…
ABB System 800xA Base
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: ABB Equipment: System 800xA Base Vulnerability: Incorrect Permission Assignment for Critical Resource 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to escalate privileges and cause system functions to stop or malfunction. 3….
ABB Multiple System 800xA Products
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: ABB Equipment: System 800xA Vulnerabilities: Incorrect Default Permissions 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to make the system node inaccessible or tamper with runtime data in the system. 3. TECHNICAL…
ABB Central Licensing System
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: ABB Equipment: Central Licensing System (CLS) Vulnerabilities: Information Exposure; Improper Restriction of XML External Entity Reference; Uncontrolled Resource Consumption; Permissions, Privilege, and Access Controls; Improper Access Control 2. RISK EVALUATION Successful exploitation of these vulnerabilities…
GE Grid Solutions Reason RT Clocks
1. EXECUTIVE SUMMARY CVSS v3 9.6 ATTENTION: Low skill level to exploit/exploitable remotely Vendor: GE Equipment: Grid Solutions Reason RT Clocks Vulnerability: Missing Authentication for Critical Function 2. RISK EVALUATION Successful exploitation of this vulnerability could allow access to sensitive information, execution of arbitrary code, and cause the device…
SWARCO CPU LS4000
EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: SWARCO TRAFFIC SYSTEMS Equipment: CPU LS4000 Vulnerability: Improper Access Control 2. RISK EVALUATION Successful exploitation of this vulnerability could allow access to the device and disturb operations with connected devices. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS…
Apache Tomcat RCE by deserialization (CVE-2020-9484) – write-up and exploit0
A few days ago, a new remote code execution vulnerability was disclosed for Apache Tomcat. Affected versions are: Apache Tomcat 10.x < 10.0.0-M5 Apache Tomcat 9.x < 9.0.35 Apache Tomcat 8.x < 8.5.55 Apache Tomcat 7.x < 7.0.104 In other words, all versions of tomcat…
Inductive Automation Ignition (Update A)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Inductive Automation Equipment: Ignition Vulnerabilities: Missing Authentication for Critical Function, Deserialization of Untrusted Data 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-147-01 Inductive Automation Ignition that was published…








Stay connected