Inductive Automation Ignition
1. EXECUTIVE SUMMARY CVSS v3 9.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Inductive Automation Equipment: Ignition 8 Gateway Vulnerability: Improper Access Control 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to write endless log statements into the database, which could result in a…
Eaton HMiSoft VU3
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Eaton Equipment: HMiSoft VU3 (HMIVU3 runtime not impacted) Vulnerabilities: Stack-based Buffer Overflow, Out-of-bounds Read 2. RISK EVALUATION Successful exploitation of these vulnerabilities could crash the device being accessed and may allow remote code execution or information…
Triangle MicroWorks DNP3 Outstation Libraries
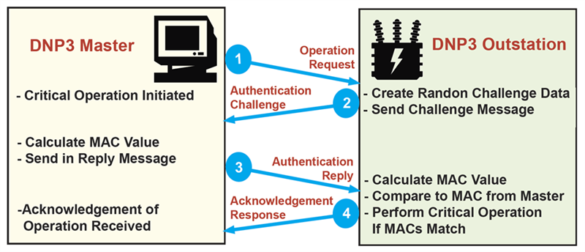
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Triangle MicroWorks Equipment: DNP3 Outstation Libraries Vulnerability: Stacked-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability could possibly allow remote attackers to stop the execution of code on affected equipment. 3. TECHNICAL DETAILS…
Triangle MicroWorks SCADA Data Gateway
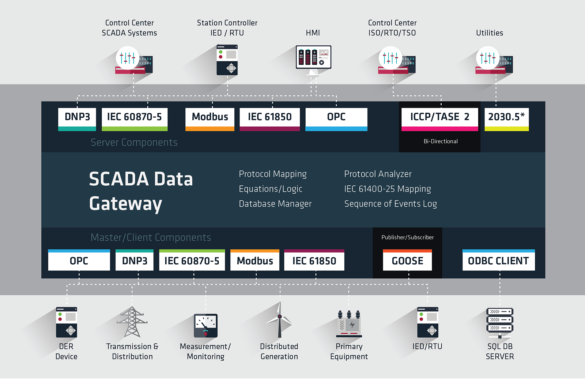
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Triangle MicroWorks Equipment: SCADA Data Gateway Vulnerabilities: Stacked-based Buffer Overflow, Out-of-Bounds Read, Type Confusion 2. RISK EVALUATION These vulnerabilities allow remote attackers to execute arbitrary code and disclose on affected installations…
Active Directory DCSync
INTRODUCTIONIn many environments Domain Controller and Active Directory are used to manage the network, users and computers. The organizations often need the existence of more than one Domain Controller for its Active Directory. For keeping an environment with more than one Domain Controller consistent, it…
Siemens Climatix
1. EXECUTIVE SUMMARY CVSS v3 6.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Climatix Vulnerability: Cross-site Scripting, Basic XSS 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote attacker to execute arbitrary code to access confidential information without authentication. 3. TECHNICAL DETAILS 3.1…
Siemens IE/PB-Link, RUGGEDCOM, SCALANCE, SIMATIC, SINEMA
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: IE/PB-Link, RUGGEDCOM, SCALANCE, SIMATIC, SINEMA Vulnerabilities: Uncontrolled Resource Consumption, Improper Input Validation 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow remote attackers to affect the availability of the devices under certain…
Siemens SIMOTICS, Desigo, APOGEE, and TALON
1. EXECUTIVE SUMMARY CVSS v3 7.1 ATTENTION: Exploitable from an adjacent network/low skill level to exploit Vendor: Siemens Equipment: SIMOTICS, Desigo, APOGEE, and TALON Vulnerability: Business Logic Errors 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to affect the availability and integrity of the device….
From Zero Credentials to Full Domain Compromise
INTRODUCTIONThis paper will cover techniques a pen-testers can use in order to accomplishinitial foothold on target networks and achieve full domain compromise withoutexecuting third party apps or reusing clear text credentisla. We will utilize how adefault Windows environment acts when IPv6 is enabled (which is…
Siemens SCALANCE & SIMATIC
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SCALANCE, SIMATIC Vulnerability: Resource Exhaustion 2. RISK EVALUATION Successful exploitation of this vulnerability can result in a denial-of-service condition. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of SCALANCE are affected: SCALANCE…








Stay connected