HMS Networks eWON Flexy and Cosy
1. EXECUTIVE SUMMARY CVSS v3 6.1 ATTENTION: Exploitable remotely Vendor: HMS Networks Equipment: eWON Flexy and Cosy Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could initiate a password change. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following eWON products are affected: eWON Flexy: All firmware…
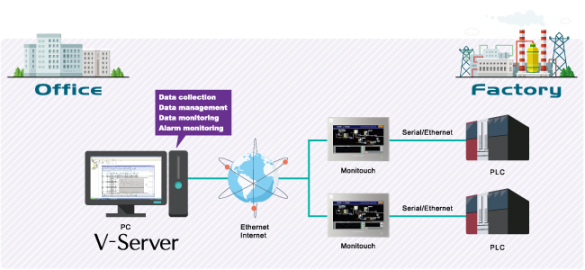
Fuji Electric V-Server Lite
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Fuji Electric Equipment: V-Server Lite Vulnerability: Heap-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote attacker to gain elevated privileges for remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED…
B&R Automation Studio
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: B&R Automation Equipment: Automation Studio Vulnerabilities: Improper Privilege Management, Missing Required Cryptographic Step, Path Traversal 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to delete arbitrary files from this system, fetch…
KUKA.Sim Pro
1. EXECUTIVE SUMMARY CVSS v3 4.3 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: KUKA Equipment: Sim Pro Vulnerability: Improper Enforcement of Message Integrity During Transmission in a Communication Channel 2. RISK EVALUATION Successful exploitation of this vulnerability could result in a loss of integrity in external 3D models…
Synergy Systems & Solutions HUSKY RTU (Update A)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Synergy Systems & Solutions (SSS) Equipment: HUSKY RTU ——— Begin Update A Part 1 of 3 ——— Vulnerabilities: Improper Authentication, Improper Input Validation, Missing Authentication for Critical Function, Improper Check for Unusual or Exceptional…
Mitsubishi Electric MELSEC
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Mitsubishi Electric Equipment: MELSEC Vulnerability: Uncontrolled Resource Consumption 2. RISK EVALUATION Successful exploitation of this vulnerability may render the device unresponsive. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of MELSEC programmable controllers with…
Schneider Electric Modicon Controllers (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Schneider Electric Equipment: Modicon M580, Modicon M340, Modicon Quantum, and Modicon Premium Vulnerability: Improper Check for Unusual or Exceptional Conditions 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-016-01…
Advantech WebAccess
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Advantech Equipment: WebAccess Vulnerability: Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability may allow remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of WebAccess, an HMI platform, are…
VISAM Automation Base (VBASE)
1. EXECUTIVE SUMMARY CVSS v3 9.0 ATTENTION: Exploitable remotely/low skill level to exploit. Vendor: VISAM Equipment: VBASE Vulnerabilities: Relative Path Traversal, Incorrect Default Permissions, Inadequate Encryption Strength, Insecure Storage of Sensitive Information, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to read…
Schneider Electric IGSS SCADA Software
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Schneider Electric Equipment: IGSS (Interactive Graphical SCADA System) Vulnerabilities: Path Traversal, Missing Authentication for Critical Function 2. RISK EVALUATION Successful exploitation of these vulnerabilities could result in unauthorized access to sensitive data and functions. 3….









Stay connected