ABB Power Generation Information Manager (PGIM) and Plant Connect
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: ABB Equipment: Power Generation Information Manager (PGIM) and Plant Connect Vulnerability: Authentication Bypass Using an Alternate Path or Channel 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote attacker to bypass authentication…
Siemens PROFINET Devices (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: PROFINET Devices Vulnerability: Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-19-283-02 Siemens PROFINET Devices that was published October 10, 2019, on the ICS…
Siemens Industrial Products (Update B)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Industrial Products Vulnerabilities: Integer Overflow or Wraparound, Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-19-253-03 Siemens Industrial Products (Update A) that was published…
Siemens SINAMICS (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SINAMICS Vulnerability: Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-19-227-04 Siemens SINAMICS that was published August 15, 2019, on the ICS webpage…
Medtronic Valleylab FT10 and FX8
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Medtronic Equipment: Valleylab FT10, Valleylab FX8 Vulnerabilities: Use of Hard-coded Credentials, Reversible One-way Hash, Improper Input Validation 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow an attacker to overwrite files or remotely execute…
Medtronic Valleylab FT10 and LS10
1. EXECUTIVE SUMMARY CVSS v3 4.8 ATTENTION: Low skill level to exploit Vendor: Medtronic Equipment: Valleylab FT10, Valleylab LS10 Vulnerabilities: Improper Authentication, Protection Mechanism Failure 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow an attacker to connect inauthentic instruments to the affected products by spoofing RFID security…
Mitsubishi Electric MELSEC-Q Series and MELSEC-L Series CPU Modules
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Mitsubishi Electric Equipment: MELSEC-Q Series and MELSEC-L Series CPU Modules Vulnerability: Uncontrolled Resource Consumption 2. RISK EVALUATION Successful exploitation of this vulnerability may prevent the FTP client from connecting to the FTP server on MELSEC-Q…
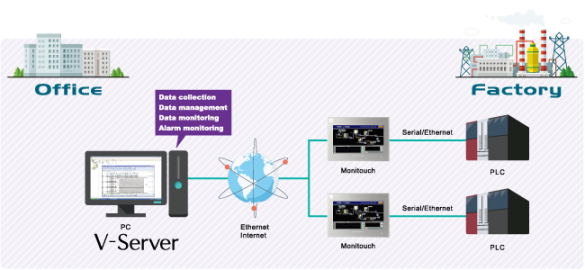
Fuji Electric V-Server
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Fuji Electric Equipment: V-Server Vulnerability: Heap-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability could crash the device being accessed; several heap-based buffer overflows have been identified. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The…
Philips Tasy EMR (Update A)
1. EXECUTIVE SUMMARY ——— Begin Update A Part 1 of 7 ——— CVSS v3 4.3 ATTENTION: Low skill level to exploit ——— End Update A Part 1 of 7 ——— Vendor: Philips Equipment: Tasy EMR ——— Begin Update A Part 2 of 7 ——— Vulnerability: Cross-site Scripting, Information Exposure…
Omron Network Configurator for DeviceNet (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.3 ATTENTION: Low skill level to exploit Vendor: Omron Equipment: Network Configurator for DeviceNet Vulnerability: Untrusted Search Path 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-19-134-01 Omron Network Configurator for DeviceNet that was published May 14, 2019,…









Stay connected