McAfee SINAMICS PERFECT HARMONY GH180
1. EXECUTIVE SUMMARY CVSS v3 7.1 ATTENTION: Low skill level to exploit Vendor: McAfee Equipment: SINAMICS PERFECT HARMONY GH180 Vulnerability: Improper Access Control 2. RISK EVALUATION These files can be executed to compromise the HMI, and by extension, the drive system. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Siemens has…
Warning! Unprivileged Linux Users With UID > INT_MAX Can Execute Any Command
Hold tight, this may blow your mind… A low-privileged user account on most Linux operating systems with UID value anything greater than 2147483647 can execute any systemctl command unauthorizedly—thanks to a newly discovered vulnerability. The reported vulnerability actually resides in PolicyKit (also known as polkit)—an…
Rockwell Automation MicroLogix 1400 Controllers and 1756 ControlLogix Communications Modules
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: MicroLogix 1400 Controllers and 1756 ControlLogix Communications Modules Vulnerability: Missing Authentication for Critical Function 2. REPOSTED INFORMATION This advisory was originally posted to the HSIN ICS-CERT library on November 6, 2018, and…
GE Proficy GDS
1. EXECUTIVE SUMMARY CVSS v3 8.2 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: General Electric (GE) Equipment: Proficy GDS Vulnerability: XXE 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to initiate an OPC UA session and retrieve an arbitrary file. 3. TECHNICAL DETAILS 3.1…
Philips HealthSuite Health Android App
1. EXECUTIVE SUMMARY CVSS v3 3.5 ATTENTION: Low skill level to exploit Vendor: Philips Equipment: Philips HealthSuite Health Android App Vulnerability: Inadequate Encryption Strength 2. RISK EVALUATION Successful exploitation of this vulnerability may allow an attacker with physical access to impact confidentiality and integrity of the product. 3. TECHNICAL…
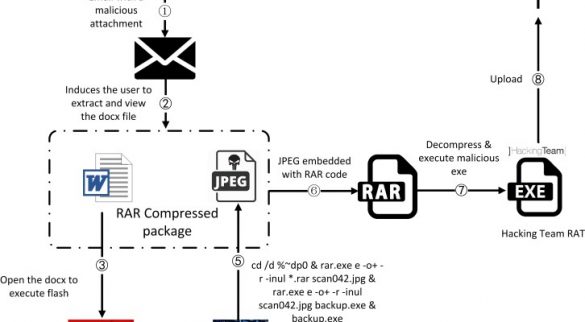
CVE-2018-15982 Adobe zero-day exploited in targeted attacks
Adobe released security updates for Flash Player that address two vulnerabilities, including a critical flaw, tracked as CVE-2018-15982, exploited in targeted attacks. Adobe fixed two flaws including a critical use-after-free bug, tracked as CVE-2018-15982, exploited by an advanced persistent threat actor aimed at a healthcare organization associated with…
Email accounts of top NRCC officials were hacked in 2018
Threat actors had access to the email accounts of at least four NRCC aides and spied on thousands of sent and received emails for several months. The email system at the National Republican Congressional Committee (NRCC), the Republican Party’s campaigning arm, was hacked. The news…
SamSam Ransomware
Summary The Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC) and the Federal Bureau of Investigation (FBI) are issuing this activity alert to inform computer network defenders about SamSam ransomware, also known as MSIL/Samas.A. Specifically, this product shares analysis of vulnerabilities…
SpiderControl SCADA WebServer
. EXECUTIVE SUMMARY CVSS v3 6.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: SpiderControl Equipment: SCADA WebServer Vulnerability: Reflected Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to execute JavaScript on the victim’s browser. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following…
Omron CX-One
. EXECUTIVE SUMMARY CVSS v3 6.6 ATTENTION: Low skill level to exploit Vendor: Omron Equipment: CX-One Vulnerabilities: Stack-based Buffer Overflow, Use After Free 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to execute code under the privileges of the application. 3. TECHNICAL DETAILS 3.1 AFFECTED…










Stay connected