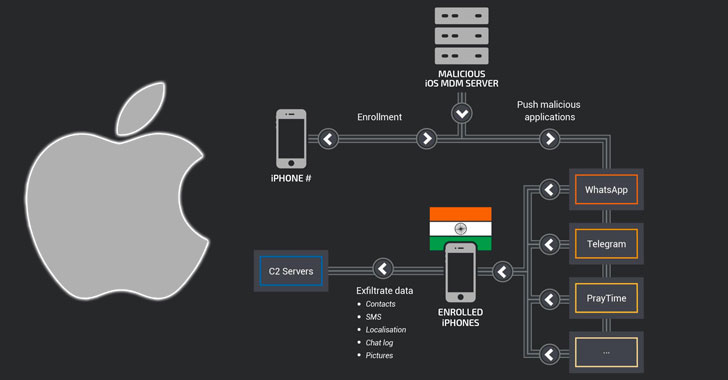
Hackers Used Malicious MDM Solution to Spy On ‘Highly Targeted’ iPhone Users
Security researchers have uncovered a “highly targeted” mobile malware campaign that has been operating since August 2015 and found spying on 13 selected iPhones in India. The attackers, who are also believed to be operating from India, were found abusing mobile device management (MDM)…
Hacker Sold Stolen U.S. Military Drone Documents On Dark Web For Just $200
You never know what you will find on the hidden Internet ‘Dark Web.’ It has been reported that a hacker was found selling sensitive US Air Force documents on the dark web for between $150 and $200. Cybercrime tracker Recorded Future today reported that…
Malicious Software Packages Found On Arch Linux User Repository
Yet another incident which showcases that you should not explicitly trust user-controlled software repositories. One of the most popular Linux distros Arch Linux has pulled as many as three user-maintained software repository AUR packages after it was found hosting malicious code. Arch Linux is an independently developed,…
Two New Spectre-Class CPU Flaws Discovered—Intel Pays $100K Bounty
Intel has paid out a $100,000 bug bounty for new processor vulnerabilities that are related to Spectre variant one (CVE-2017-5753). The new Spectre-class variants are tracked as Spectre 1.1 (CVE-2018-3693) and Spectre 1.2, of which Spectre 1.1 described as a bounds-check bypass store attack has…
Microsoft Releases Patch Updates for 53 Vulnerabilities In Its Software
It’s time to gear up your systems and software for the latest July 2018 Microsoft security patch updates. Microsoft today released security patch updates for 53 vulnerabilities, affecting Windows, Internet Explorer (IE), Edge, ChakraCore, .NET Framework, ASP.NET, PowerShell, Visual Studio, and Microsoft Office and…
Gaza Cybergang Returns With New Attacks On Palestinian Authority
Security researchers from Check Point Threat Intelligence Team have discovered the comeback of an APT (advanced persistent threat) surveillance group targeting institutions across the Middle East, specifically the Palestinian Authority. The attack, dubbed “Big Bang,” begins with a phishing email sent to targeted victims…
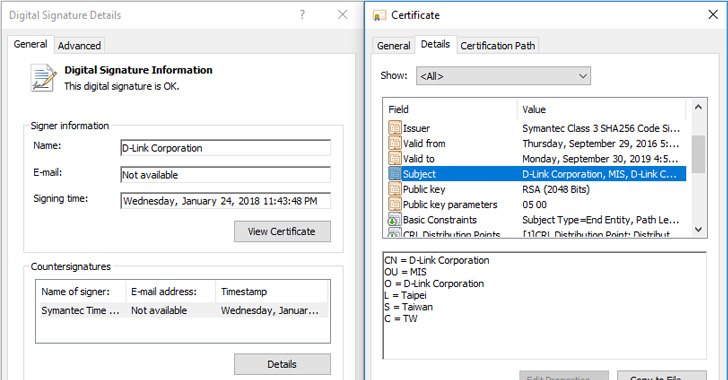
Stolen D-Link Certificate Used to Digitally Sign Spying Malware
Digitally signed malware has become much more common in recent years to mask malicious intentions. Security researchers have discovered a new malware campaign misusing stolen valid digital certificates from Taiwanese tech-companies, including D-Link, to sign their malware and making them look like legitimate applications. As…
DomainFactory Hacked—Hosting Provider Asks All Users to Change Passwords
Besides Timehop, another data breach was discovered last week that affects users of one of the largest web hosting companies in Germany, DomainFactory, owned by GoDaddy. The breach initially happened back in last January this year and just emerged last Tuesday when an unknown…
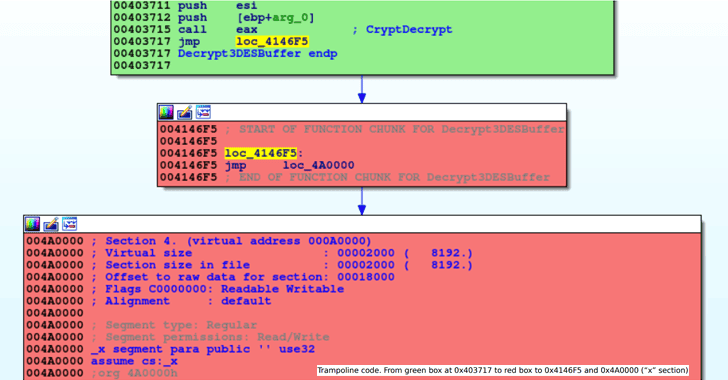
Most LokiBot samples in the wild are “hijacked” versions of the original malware
Hacker himself got hacked. It turns out that most samples of the LokiBot malware being distributed in the wild are modified versions of the original sample, a security researcher has learned. Targeting users since 2015, LokiBot is a password and cryptocoin-wallet stealer that can harvest…
ARM EXPLOITATION FOR IoT
Authored by Andrea Sindoni Introduction and motivation A year ago while I was attending a conference, I’ve noticed that price tag for the proposed ARM exploitation cource for IoT was quite substantial and decided to write my own to allow those who can’t afford to spend…







Stay connected