Siemens SCALANCE S-600 (Update B)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: SCALANCE S-600 Firewall Vulnerabilities: Resource Exhaustion, Cross-site Scripting 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-20-042-10 Siemens SCALANCE S-600 (Update A) that was published August 11, 2020 to…
Siemens SIMATIC Communication Processor Vulnerability (Update C)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: SIMATIC Communication Processor Vulnerability: Authentication Bypass Issues 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-15-335-03 Siemens SIMATIC Communication Processor (Update B) that was published May 3, 2016, to…
Schneider Electric SoMachine Basic
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low attack complexity Vendor: Schneider Electric Equipment: SoMachine Basic Vulnerability: Improper Restriction of XML External Entity Reference 2. RISK EVALUATION Successful exploitation of this vulnerability may result in disclosure and retrieval of arbitrary data on the affected node via out-of-band (OOB)…
Advantech WebAccessSCADA
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Advantech Equipment: WebAccess/SCADA Vulnerability: Incorrect Permission Assignment for Critical Resource 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to login as an ‘admin’ to fully control the system. 3. TECHNICAL DETAILS 3.1 AFFECTED…
JTEKT TOYOPUC products
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: JTEKT Corporation Equipment: TOYOPUC products Vulnerability: Improper Resource Shutdown or Release 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an unauthorized user to stop Ethernet communications between devices from being established. 3. TECHNICAL DETAILS 3.1…
Siemens Solid Edge File Parsing
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low attack complexity Vendor: Siemens Equipment: Solid Edge Vulnerabilities: Out-of-bounds Write, Improper Restriction of XML External Entity Reference, Out-of-bounds Read 2. RISK EVALUATION Successful exploitation of these vulnerabilities could lead to a crash, arbitrary code execution, or data extraction on the target…
Siemens Web Server of SCALANCE X200
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: Web Server of SCALANCE X200 Vulnerabilities: Heap-based Buffer Overflow, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities could cause a buffer overflow condition resulting in remote code execution. 3. TECHNICAL DETAILS…
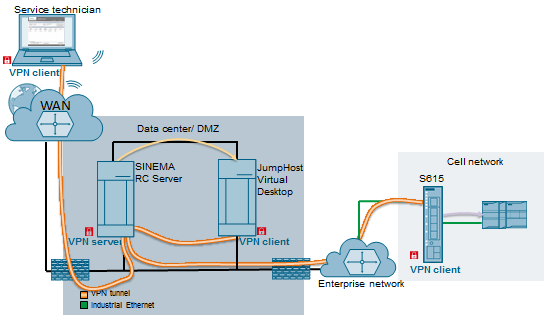
Siemens SINEMA Remote Connect Server
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: SINEMA Remote Connect Server Vulnerabilities: Missing Release of Resource after Effective Lifetime, Infinite Loop 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to cause a memory leak or an infinite loop…
Siemens LOGO! Soft Comfort
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: Nucleus Vulnerability: Use of Insufficiently Random Values 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow a local attacker to take over the system where the software is installed. 3. TECHNICAL DETAILS 3.1 AFFECTED…
Siemens and PKE Control Center Server
1. EXECUTIVE SUMMARY CVSS v3 9.9 ATTENTION: Exploitable remotely/low attack complexity Vendors: Siemens/PKE Equipment: Control Center Server (CCS) Vulnerabilities: Cleartext Storage of Sensitive Information in GUI, Improper Authentication, Relative Path Traversal, Use of a Broken or Risky Cryptographic Algorithm, Exposed Dangerous Method or Function, Path Traversal, Cleartext Storage in…








Stay connected