Schneider Electric Modicon M221
1. EXECUTIVE SUMMARY CVSS v3 8.2 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Schneider Electric Equipment: Modicon M221 Vulnerability: Insufficient Verification of Data Authenticity 2. RISK EVALUATION Successful exploitation of this vulnerability could cause a change of IPv4 configuration (IP address, mask, and gateway) when remotely connected to…
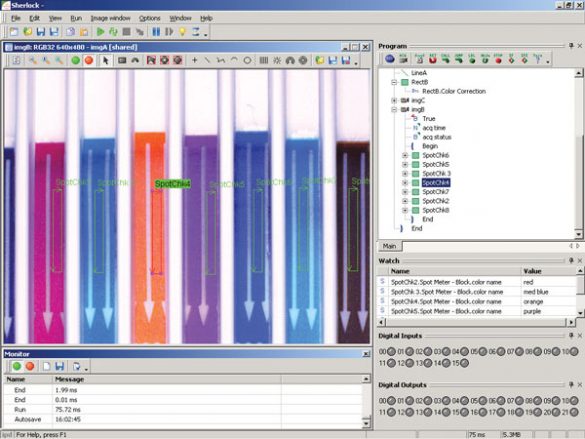
Teledyne DALSA Sherlock
1. EXECUTIVE SUMMARY CVSS v3 7.3 ATTENTION: Low skill level to exploit Vendor: Teledyne DALSA Equipment: Sherlock Vulnerability: Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability could crash the device being accessed; a buffer overflow condition may allow remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED…
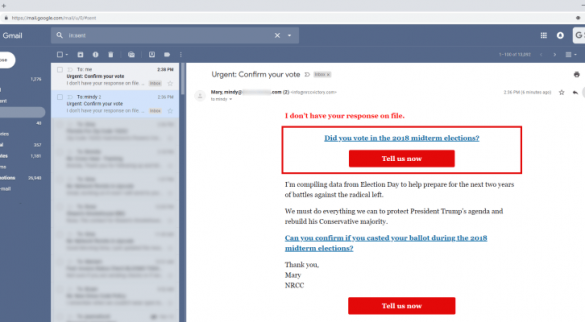
Hacking Gmail’s UX with from fields for phishing attacks
A glitch in Gmail could be exploited by hackers to carry out phishing attacks, the issue is related the way Gmail automatically files messages into Sent folder A bug in Gmail could be exploited by attackers to carry out phishing attacks, the flaw ties the…
Group-IB presented latest cybercrime and nation-state hacking trends in Asia
According to Group-IB’s report findings, Asia is one of the most actively attacked regions in the world, the company presented latest cybercrime trends. Hong Kong, 16.11.2018 – Group-IB, an international company that specializes in preventing cyber attacks, presented the findings of its latest Hi-Tech Crime Trends 2018 report at the…
Two hacker groups attacked Russian banks posing as the Central Bank of Russia
The emails were disguised to look as if they come from the Central Bank of Russia and FinCERT, the Financial Sector Computer Emergency Response Team. Group-IB experts have discovered that the attack on 15 November could have been carried out by the hacker group Silence, and the one…
GPUs are vulnerable to side-channel attacks
Researchers at UCLA Riverside discover GPUs can be victims of the same kinds of attacks as Meltdown and Spectre, which have impacted Intel and AMD CPUs. Computer scientists at the University of California at Riverside have found that GPUs are vulnerable to side-channel attacks,…
Siemens devices using the PROFINET Discovery and Configuration Protocol (Update M)
. EXECUTIVE SUMMARY CVSS v3 6.5 ATTENTION: Exploitable from an adjacent network/low skill level to exploit. Vendor: Siemens Equipment: Devices using the PROFINET Discovery and Configuration Protocol (DCP) Vulnerabilities: Improper Input Validation 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory…
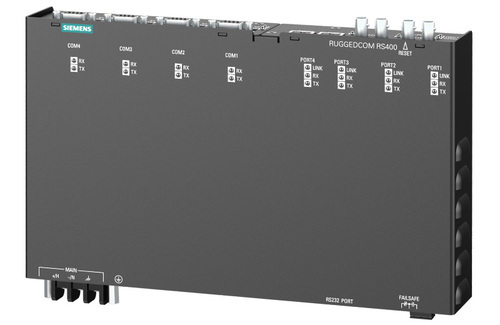
Siemens SCALANCE, SIMATIC, RUGGEDCOM, and SINAMICS Products (Update E)
1. EXECUTIVE SUMMARY CVSS v3 6.8 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available. Vendor: Siemens Equipment: SCALANCE, SIMATIC, RUGGEDCOM, and SINAMICS Products Vulnerabilities: Security Features 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-17-318-01 Siemens SCALANCE,…
Siemens Industrial Products (Update I)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Remotely exploitable/low skill level to exploit Vendor: Siemens Equipment: Industrial Products Vulnerability: Improper Input Validation 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-17-339-01 Siemens Industrial Products (Update H) published October 9,…
Siemens SIMATIC PCS 7, SIMATIC WinCC, SIMATIC WinCC Runtime Professional, and SIMATIC NET PC Software (Update D)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit. Vendor: Siemens Equipment: SIMATIC PCS 7, SIMATIC WinCC, SIMATIC WinCC Runtime Professional, and SIMATIC NET PC Software Vulnerability: Improper Input Validation 2. UPDATE INFORMATION This updated advisory is a follow-up to the…








Stay connected