Siemens SIMATIC S7-1200 CPUs
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an unauthenticated attacker to change the CPU mode by tricking a legitimate and authenticated user with sufficient permissions on the target CPU to click on a malicious link. 3. TECHNICAL DETAILS 3.1…
Bosch Rexroth IndraDrive
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to cause a denial-of-service, rendering the device unresponsive by sending arbitrary UDP messages. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Bosch Rexroth reports that the following versions of IndraDrive, servo drive…
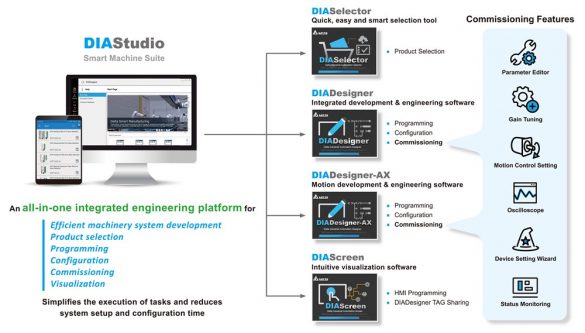
Delta Electronics DIAScreen
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this these vulnerabilities could crash the device being accessed; a buffer overflow condition may allow remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of DIAScreen, which is a component of Delta’s DIAStudio…
LiteSpeed Cache Plugin Vulnerability Poses Significant Risk to WordPress Websites
A high-severity security flaw has been disclosed in the LiteSpeed Cache plugin for WordPress that could allow an unauthenticated threat actor to elevate their privileges and perform malicious actions. The vulnerability, tracked as CVE-2024-50550 (CVSS score: 8.1), has been addressed in version 6.5.2 of the…
Delta Electronics InfraSuite Device Master
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an unauthenticated attacker to remotely execute arbitrary code. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of InfraSuite Device Master, a real-time device monitoring software, are affected: 3.2 Vulnerability Overview 3.2.1 DESERIALIZATION…
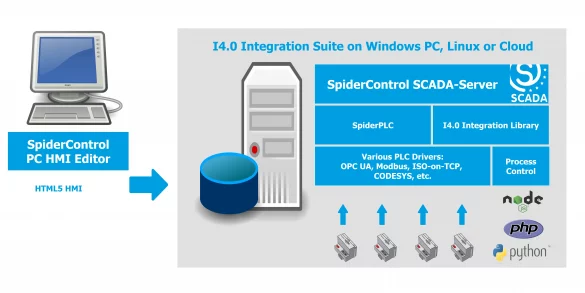
iniNet Solutions SpiderControl SCADA PC HMI Editor
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to gain remote control of the device. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of iniNet Solutions SpiderControl SCADA PC HMI Editor, a software management platform, are affected:…
VIMESA VHF/FM Transmitter Blue Plus
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to perform a Denial-of-Service. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following version of VIMESA VHF/FM Transmitter Blue Plus, a VHF/FM Transmitter, is affected: 3.2 Vulnerability Overview 3.2.1 Improper Access Control…
Cisco Adaptive Security Appliance Software SSH Remote Command Injection Vulnerability
Summary A vulnerability in the SSH subsystem of Cisco Adaptive Security Appliance (ASA) Software could allow an authenticated, remote attacker to execute operating system commands as root. This vulnerability is due to insufficient validation of user input. An attacker could exploit this vulnerability by submitting crafted…
Cisco Firepower Threat Defense Software for Firepower 1000, 2100, 3100, and 4200 Series Static Credential Vulnerability
Summary A vulnerability in Cisco Firepower Threat Defense (FTD) Software for Cisco Firepower 1000, 2100, 3100, and 4200 Series could allow an unauthenticated, local attacker to access an affected system using static credentials. This vulnerability is due to the presence of static accounts with hard-coded…
Microsoft creates fake Azure tenants to pull phishers into honeypots
Microsoft is using deceptive tactics against phishing actors by spawning realistic-looking honeypot tenants with access to Azure and lure cybercriminals in to collect intelligence about them. With the collected data, Microsoft can map malicious infrastructure, gain a deeper understanding of sophisticated phishing operations, disrupt campaigns at…








Stay connected