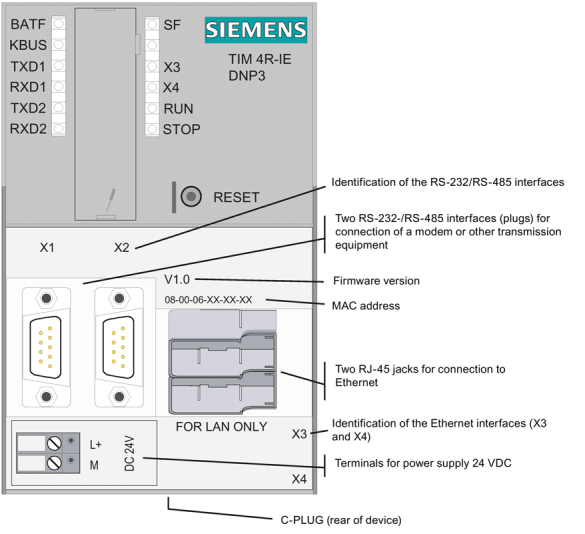
Siemens TIM 4R-IE Devices
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: TIM 4R-IE Vulnerabilities: Incorrect Type Conversion or Cast, Improper Input Validation, Improper Authentication, Security Features, Null Pointer Dereference, Data Processing Errors, Exposure of Sensitive Information to an Unauthorized Actor, Race Condition 2. RISK EVALUATION Successful…
Siemens SIMOTICS CONNECT 400
1. EXECUTIVE SUMMARY CVSS v3 6.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: SIMOTICS CONNECT 400 Vulnerabilities: Improper Null Termination, Out-of-bounds Read, Access of Memory Location After End of Buffer, Use of Insufficiently Random Values 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to…
Siemens Nucleus DNS
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: Nucleus Vulnerability: Use of Insufficiently Random Values 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to poison the DNS cache or spoof DNS resolving. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The…
Siemens and Milestone Siveillance Video Open Network Bridge
1. EXECUTIVE SUMMARY CVSS v3 9.9 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens and Milestone Equipment: Siveillance Video Open Network Bridge (ONVIF) Vulnerability: Use of Hard-coded Cryptographic Key 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an authenticated remote attacker to retrieve and…
Medtronic Conexus Radio Frequency Telemetry Protocol (Update C)
1. EXECUTIVE SUMMARY CVSS v3 9.3 ATTENTION: Exploitable with adjacent access/low attack complexity Vendor: Medtronic Equipment: MyCareLink Monitor, CareLink Monitor, CareLink 2090 Programmer, specific Medtronic implanted cardiac devices listed below Vulnerabilities: Improper Access Control, Cleartext Transmission of Sensitive Information 2. UPDATE INFORMATION This updated advisory is a follow-up to…
Rockwell Automation FactoryTalk AssetCentre
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/Low attack complexity Vendor: Rockwell Automation Equipment: FactoryTalk AssetCentre Vulnerabilities: OS Command Injection, Deserialization of Untrusted Data, SQL Injection, Improperly Restricted Functions 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow unauthenticated attackers to perform arbitrary command execution, SQL injection,…
Philips Gemini PET/CT Family
1. EXECUTIVE SUMMARY CVSS v3 2.4 ATTENTION: Low skill level to exploit Vendor: Philips Equipment: Gemini PET/CT Family Vulnerability: Storage of Sensitive Data in a Mechanism Without Access Control 2. RISK EVALUATION Successful exploitation of this vulnerability involving removable media could allow access to sensitive information (including patient information)….
Weintek EasyWeb cMT
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Weintek Equipment: cMT Vulnerabilities: Code Injection, Improper Access Control, Cross-site Scripting 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an unauthenticated remote attacker to access sensitive information and execute arbitrary code to gain…
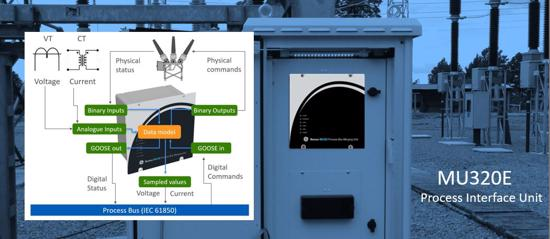
GE MU320E
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: GE Equipment: MU320E Vulnerabilities: Use of Hard-coded Password, Execution with Unnecessary Privileges, Inadequate Encryption Strength 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to escalate unnecessary privileges and use hard-coded credentials…
GE Reason DR60
1. EXECUTIVE SUMMARY CVSS v3 9.8 GE Reason DR60 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: GE Equipment: Reason DR60 Vulnerabilities: Hard-coded Password, Code Injection, Execution with Unnecessary Privileges 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to take full control of the digital…







Stay connected