Siemens Mendix Applications
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation requires to guess the identification of a target role which contains the elevated access rights. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following Siemens products, are affected: 3.2 Vulnerability Overview 3.2.1 IMPROPER PRIVILEGE MANAGEMENT CWE-269 Affected applications could…
ANSI Escape Injection Vulnerability in WinRAR
On 28 February 2024, RARLAB released an update for WinRAR, patching an ANSI escape sequence injection vulnerability that I had found in the console versions of RAR and UnRAR, affecting versions 6.24 and earlier. This vulnerability, tracked as CVE-2024–33899 for Linux and Unix systems and…
IOSIX IO-1020 Micro ELD
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an adjacent attacker to take control of vehicle systems by connecting to and modifying the affected device. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following IOSiX products are affected: 3.2 Vulnerability Overview…
Critical Vulnerability Allows Access to QNAP NAS Devices
Taiwan-based QNAP Systems over the weekend announced patches for multiple vulnerabilities impacting its products, including a critical-severity bug leading to unauthenticated device access. Tracked as CVE-2024-21899 (CVSS score of 9.8), the vulnerability is described as an improper authentication issue that “could allow users to compromise…
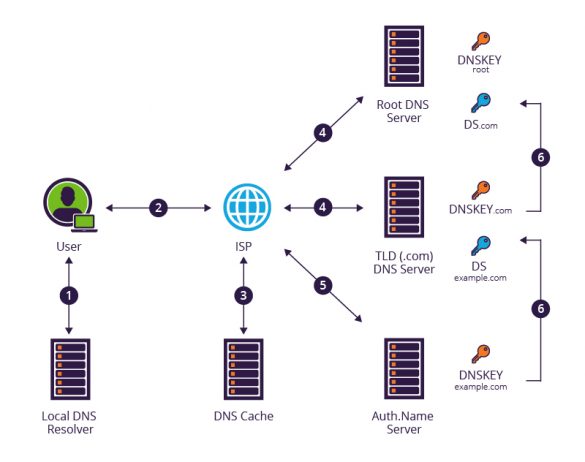
The KeyTrap Denial-of-Service Algorithmic Complexity Attacks on DNSVersion: January 2024
Abstract—Availability is a major concern in the design of DNSSEC. To ensure availability, DNSSEC follows Postel’s Law [RFC1122]: ”Be liberal in what you accept, and conservative inwhat you send.” Hence, nameservers should send not just one matching key for a record set, but all the…
New WiFi Authentication Vulnerabilities Discovered
One vulnerability affects Android, ChromeOS and Linux devices connecting to enterprise WiFi networks, another affects home WiFi using a Linux device as a wireless access point. Two new vulnerabilities in open-source WiFi software allow attackers to trick victims into connecting to malicious clones of trusted…
Siemens Parasolid
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to leverage the vulnerability to perform remote code execution in the context of the current process. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following products of Siemens are affected: 3.2…
CVE-2023-50387: KeyTrap – Extreme CPU consumption in DNSSEC validator
CVE: CVE-2023-50387 Title: KeyTrap – Extreme CPU consumption in DNSSEC validator Document version: 2.0 Posting date: 13 February 2024 Program impacted: BIND 9 Versions affected: BIND (Versions prior to 9.11.37 were not assessed.) BIND Supported Preview Edition (Versions prior to 9.11.37-S1 were not assessed.) Severity: High Exploitable: Remotely Description: The processing of…
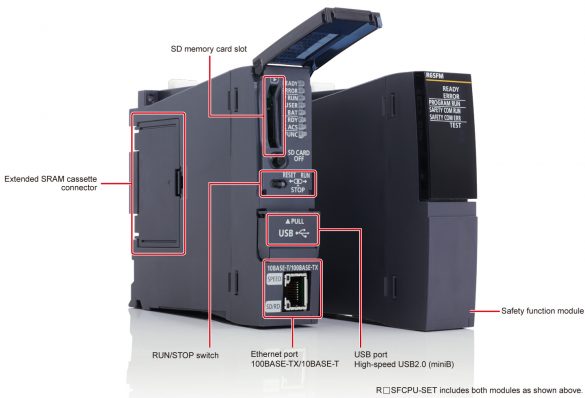
Mitsubishi Electric MELSEC iQ-R Series Safety CPU
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a non-administrator user to disclose the credentials (user ID and password) of a user with a lower access level than themselves. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Mitsubishi Electric reports that the…
Cisco Expressway Series Cross-Site Request Forgery Vulnerabilities
Summary Affected Products Details The vulnerabilities are not dependent on one another. Exploitation of one of the vulnerabilities is not required to exploit another vulnerability. In addition, a software release that is affected by one of the vulnerabilities may not be affected by the other…









Stay connected