ICS Medical Advisory (ICSMA-19-190-01)
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: GE Equipment: Aestiva and Aespire Anesthesia Vulnerability: Improper Authentication 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker the ability to remotely modify GE Healthcare anesthesia device parameters. This results from the…
Siemens CP, SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM (Update C)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: CP, SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM Vulnerability: Out-of-bounds Read 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-19-099-06 Siemens CP, SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM…
Siemens Industrial Products with OPC UA (Update C)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC, SINEC-NMS, SINEMA, SINEMURIK Industrial Control Products with OPC UA Vulnerability: Uncaught Exception 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-19-099-03 Siemens Industrial Products with OPC…
Siemens CP1604 and CP1616 (Update A)
1. EXECUTIVE SUMMARY CVSS v3 9.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: CP1604 and CP1616 Vulnerabilities: Cleartext Transmission of Sensitive Information, Cross-site Scripting, Cross-site Request Forgery 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-19-043-06…
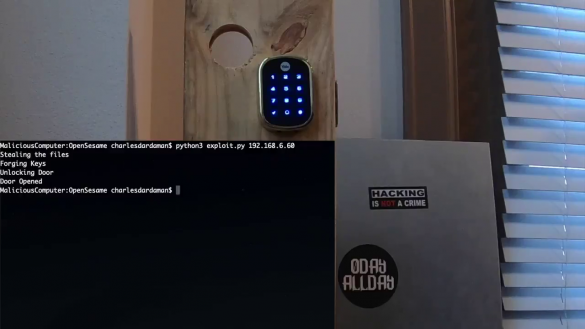
Breaking & Entering with Zipato SmartHubs
Researcher Contact Information Name Contact Role Charles Dardaman @CharlesDardaman Reverse Engineered API INIT_6 @INIT_3 Discovered Root SSH Key Executive Summary During the 0DAYALLDAY Research Event three vulnerabilities were discovered in the ZipaMicro Z-Wave Controller Model #: ZM.ZWUS and the Zipabox Z-Wave Controller Model #: 2AAU7-ZBZWUS. Two vulnerabilities…
Quest KACE Systems Management Appliance
1. EXECUTIVE SUMMARY CVSS v3 2.7 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Quest Equipment: KACE Systems Management Appliance (SMA) Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an administrative user unintentional access to the underlying operating system…
Schneider Electric Modicon Controllers
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Schneider Electric Equipment: Modicon Controllers Vulnerability: Improper Check for Unusual or Exceptional Conditions 2. RISK EVALUATION Successful exploitation of this vulnerability could result in a denial-of-service condition. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following…
ABB CP651 HMI
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable from adjacent network/low skill level to exploit Vendor: ABB Equipment: CP651 HMI Vulnerability: Use of Hard-coded Credentials 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to prevent legitimate access to an affected system…
ABB PB610 Panel Builder 600
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Low skill level to exploit Vendor: ABB Equipment: PB610 Panel Builder 600 Vulnerabilities: Use of Hard-coded Credentials, Improper Authentication, Relative Path Traversal, Improper Input Validation, Stack-based Buffer Overflow 2. RISK EVALUATION An attacker who successfully exploits these vulnerabilities could prevent legitimate access…
ABB CP635 HMI
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable from adjacent network/low skill level to exploit Vendor: ABB Equipment: CP635 HMI Vulnerability: Use of Hard-coded Credentials 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to prevent legitimate access to an affected system node, remotely cause an…









Stay connected