Siemens PROFINET-IO Stack (Update B)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Siemens PROFINET-IO Stack Vulnerability: Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-20-042-04 Siemens PROFINET-IO Stack (Update A) that was published March 10, 2020,…
Siemens Industrial Real-Time (IRT) Devices (Update D)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Industrial Real-Time (IRT) Devices Vulnerability: Improper Input Validation 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-19-283-01 Siemens Industrial Real-Time (IRT) Devices (Update C) that was published…
Siemens PROFINET Devices (Update G)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: PROFINET Devices Vulnerability: Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-19-283-02 Siemens PROFINET Devices (Update F) that was published July 14, 2020, to…
Siemens SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM Vulnerability: Out-of-bounds Read 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-19-099-06 Siemens SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM (Update H)…
Siemens Industrial Products (Update P)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Remotely exploitable/low skill level to exploit Vendor: Siemens Equipment: Industrial Products Vulnerability: Improper Input Validation 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-17-339-01 Siemens Industrial Products (Update O) published July 14,…
Siemens OPC UA Protocol Stack Discovery Service (Update D)
1. EXECUTIVE SUMMARY CVSS v3 8.2 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC Vulnerabilities: Improper restriction of XML external entity reference 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-17-243-01 Siemens OPC UA Protocol Stack Discovery Service (Update C) that was…
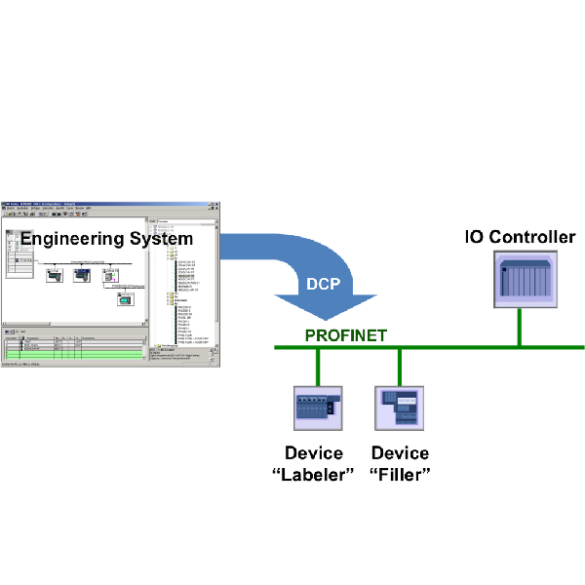
Siemens PROFINET DCP (Update R)
1. EXECUTIVE SUMMARY CVSS v3 6.5 ATTENTION: Exploitable from an adjacent network/low skill level to exploit. Vendor: Siemens Equipment: Devices using the PROFINET Discovery and Configuration Protocol (DCP) Vulnerabilities: Improper Input Validation 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory…
Trailer Power Line Communications
1. EXECUTIVE SUMMARY CVSS v3 4.3 Vendor: Multiple Trailer and Brake Manufacturers Equipment: Power Line Communications Bus / PLC4TRUCKS / J2497 Vulnerability: Exposure of Sensitive Information Through Sent Data 2. RISK EVALUATION The National Motor Freight Traffic Association (NMFTA) and Assured Information Security (AIS) have released research detailing…
Advantech WebAccess HMI Designer
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Advantech Equipment: WebAccess HMI Designer Vulnerabilities: Heap-based Buffer Overflow, Out-of-bounds Read, Out-of-bounds Write, Type Confusion, Stack-based Buffer Overflow, Double Free 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to read/modify information,…
Geutebrück G-Cam and G-Code
1. EXECUTIVE SUMMARY CVSS v3 7.2 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available Vendor: Geutebrück Equipment: G-Cam and G-Code Vulnerability: OS Command Injection 2. RISK EVALUATION Successful exploitation of this vulnerability could allow remote code execution as root. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Geutebruck reports…









Stay connected