Mitsubishi Electric MELSEC
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Mitsubishi Electric Equipment: MELSEC Vulnerability: Uncontrolled Resource Consumption 2. RISK EVALUATION Successful exploitation of this vulnerability may render the device unresponsive. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of MELSEC programmable controllers with…
Schneider Electric Modicon Controllers (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Schneider Electric Equipment: Modicon M580, Modicon M340, Modicon Quantum, and Modicon Premium Vulnerability: Improper Check for Unusual or Exceptional Conditions 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-016-01…
Advantech WebAccess
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Advantech Equipment: WebAccess Vulnerability: Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability may allow remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of WebAccess, an HMI platform, are…
VISAM Automation Base (VBASE)
1. EXECUTIVE SUMMARY CVSS v3 9.0 ATTENTION: Exploitable remotely/low skill level to exploit. Vendor: VISAM Equipment: VBASE Vulnerabilities: Relative Path Traversal, Incorrect Default Permissions, Inadequate Encryption Strength, Insecure Storage of Sensitive Information, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to read…
Schneider Electric IGSS SCADA Software
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Schneider Electric Equipment: IGSS (Interactive Graphical SCADA System) Vulnerabilities: Path Traversal, Missing Authentication for Critical Function 2. RISK EVALUATION Successful exploitation of these vulnerabilities could result in unauthorized access to sensitive data and functions. 3….
Systech NDS-5000 Terminal Server
1. EXECUTIVE SUMMARY CVSS v3 6.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Systech Corporation Equipment: NDS-5000 Terminal Server Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could allow information disclosure, limit system availability, and may allow remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED…
ABB eSOMS
1. EXECUTIVE SUMMARY CVSS v3 7.6 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: ABB Equipment: eSOMS Vulnerabilities: Use of Web Browser Cache Containing Sensitive Information, Improper Restriction of Rendered UI Layers or Frames, Improper Neutralization of HTTP Headers for Scripting Syntax, Sensitive Cookie Without ‘HttpOnly’ Flag, Protection Mechanism…
Delta Electronics Industrial Automation CNCSoft ScreenEditor
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Delta Electronics Equipment: Delta Industrial Automation CNCSoft ScreenEditor Vulnerabilities: Stack-based Buffer Overflow, Out-of-bounds Read 2. RISK EVALUATION Successful exploitation of these vulnerabilities could cause buffer overflow conditions that may allow information disclosure, remote code execution, or…
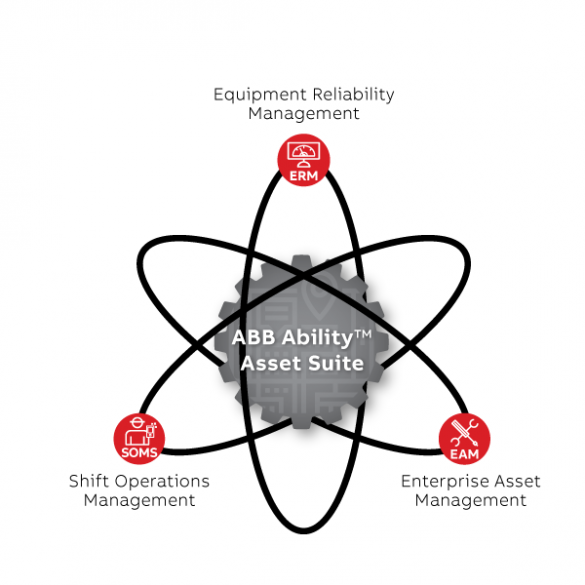
ABB Asset Suite
1. EXECUTIVE SUMMARY CVSS v3 7.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: ABB Equipment: Asset Suite Vulnerability: Authorization Bypass Through User-Controlled Key 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker access to unauthorized information in the application by direct resource access. 3. TECHNICAL…
Rockwell Automation Allen-Bradley Stratix 5950
1. EXECUTIVE SUMMARY CVSS v3 6.7 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: Allen-Bradley Stratix 5950 Vulnerability: Improper Access Control 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to write a modified image to the component. 3. TECHNICAL DETAILS 3.1 AFFECTED…









Stay connected