Vulnerability – Siemens SINAMICS
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SINAMICS Image alt attributes: Images on this page do not have alt attributes that reflect the topic of your text. Add your keyphrase or synonyms to the alt tags of relevant images! Keyphrase…
Siemens SIMATIC CP 343-1CP 443-1 Modules and SIMATIC S7-300S7-400 CPUs (Update B)
1. EXECUTIVE SUMMARY CVSS v3 6.3 ATTENTION: Exploitable remotely; low skill level is needed to exploit. Vendor: Siemens Equipment: SIMATIC Vulnerabilities: Insufficient Verification of Data Authenticity, Sensitive Cookie in HTTPS Session Without ‘Secure’ Attribute 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-16-327-02…
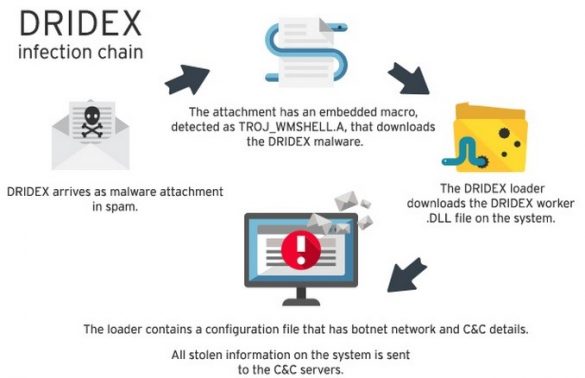
Dridex Malware
Summary This Alert is the result of recent collaboration between the Department of the Treasury Financial Sector Cyber Information Group (CIG) and the Department of the Treasury’s Financial Crimes Enforcement Network (FinCEN) to identify and share information with the financial services sector. Treasury and the…
Thales DIS SafeNet Sentinel LDK License Manager Runtime
1. EXECUTIVE SUMMARY CVSS v3 7.3 ATTENTION: Low skill level to exploit Vendor: Thales DIS Equipment: SafeNet Sentinel LDK License Manager Runtime Vulnerability: Link Following 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a local attacker to escalate privileges. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following…
Weidmueller Industrial Ethernet Switches
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Weidmueller Equipment: Industrial Ethernet Switches Vulnerabilities: Improper Restriction of Excessive Authentication Attempts, Uncontrolled Resource Consumption, Missing Encryption of Sensitive Data, Unprotected Storage of Credentials, and Predictable from Observable State 2. RISK EVALUATION Successful exploitation of…
Moxa AWK-3121
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits available Vendor: Moxa Equipment: AWK-3121 Vulnerabilities: Cleartext Transmission of Sensitive Information, Improper Access Control, Sensitive Cookie without ‘HTTPONLY’ Flag, Improper Restriction of Operations within the Bounds of a Memory Buffer, CSRF, Command Injection, Cross-site Scripting…
Reliable Controls LicenseManager
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Reliable Controls Equipment: LicenseManager Vulnerability: Unquoted Search Path or Element 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to crash the system, view sensitive data, or execute arbitrary commands. 3. TECHNICAL DETAILS…
ABB Relion 670 Series
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: ABB Equipment: Relion 670 Series Vulnerability: Path Traversal 2. RISK EVALUATION Successful exploitation of this vulnerability may allow an attacker to read and delete files on the device. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The…
Docker Patched the Most Severe Copy Vulnerability to Date With CVE-2019-14271
Executive Summary In the last few years, several vulnerabilities in the copy (cp) command were found in various container platforms, including Docker, Podman and Kubernetes. The most severe among those was only recently discovered and disclosed in July. Surprisingly, it gained almost no immediate attention,…
Flexera FlexNet Publisher
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Flexera Equipment: FlexNet Publisher Vulnerabilities: Improper Input Validation, Memory Corruption 2. RISK EVALUATION These vulnerabilities could allow an attacker to deny the acquisition of a valid license for legal use of the product. The memory…










Stay connected