Mitsubishi Electric MELSEC-Q Series PLCs
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Mitsubishi Electric Equipment: MELSEC-Q series PLCs Vulnerability: Resource Exhaustion 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote attacker to send specially crafted packets to the device, causing Ethernet communication to stop….
Yokogawa License Manager Service
1. EXECUTIVE SUMMARY CVSS v8.1 ATTENTION: Exploitable remotely Vendor: Yokogawa Equipment: License Manager Service Vulnerability: Unrestricted Upload of Files with Dangerous Type 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to remotely upload files, allowing execution of arbitrary code. 3. TECHNICAL…
BD FACSLyric
1. EXECUTIVE SUMMARY CVSS v3 6.8 ATTENTION: Low skill level to exploit Vendor: Becton, Dickinson and Company (BD) Equipment: FACSLyric Vulnerability: Improper Access Control 2. RISK EVALUATION Successful exploitation of this vulnerability may allow an attacker to gain unauthorized access to administrative level privileges on a workstation, which could…
Stryker Medical Beds
1. EXECUTIVE SUMMARY CVSS v3 6.8 ATTENTION: Public exploits are available Vendor: Stryker Equipment: Secure II MedSurg Bed, S3 MedSurg Bed, and InTouch ICU Bed Vulnerability: Reusing a Nonce 2. RISK EVALUATION Successful exploitation of this vulnerability could allow data traffic manipulation, resulting in partial disclosure of encrypted communication…
PHOENIX CONTACT FL SWITCH
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: PHOENIX CONTACT Equipment: FL SWITCH Vulnerabilities: Cross-site Request Forgery, Improper Restriction of Excessive Authentication Attempts, Cleartext Transmission of Sensitive Information, Resource Exhaustion, Incorrectly Specified Destination in a Communication Channel, Insecure Storage of Sensitive Information, and…
Advantech WebAccess/SCADA
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Advantech Equipment: WebAccess/SCADA Vulnerabilities: Improper Authentication, Authentication Bypass, SQL Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow an attacker to access and manipulate sensitive data. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The…
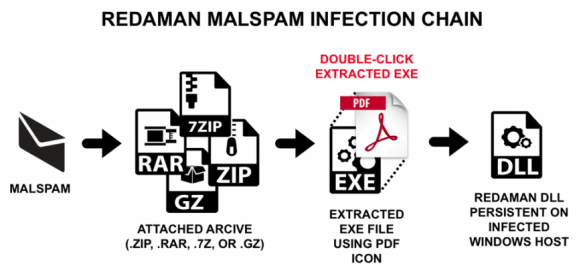
Russian Language Malspam Pushing Redaman Banking Malware
Redaman is banking malware first noted in 2015 that targets recipients who conduct transactions using Russian financial institutions. First reported as the RTM banking Trojan, vendors like Symantecand Microsoft described an updated version of this malware as Redaman in 2017. We have found versions of Redaman in Russian language…
Critical flaw in Linux APT package manager could allow remote hack
Expert discovered a remote code execution vulnerability in the APT package manager used by several Linux distributions, including Debian and Ubuntu. The independent security consultant Max Justicz has discovered a remote code execution vulnerability in the APT package manager used by several Linux distributions, including Debian and Ubuntu….
Johnson Controls Facility Explorer
1. EXECUTIVE SUMMARY CVSS v3 7.4 ATTENTION: Exploitable remotely Vendor: Johnson Controls Equipment: Facility Explorer Vulnerabilities: Path Traversal, Improper Authentication 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to read, write, and delete sensitive files to gain administrator privileges in the Facility Explorer system. 3….
Dräger Infinity Delta
1. EXECUTIVE SUMMARY CVSS v3 8.4 ATTENTION: Low skill level to exploit Vendor: Dräger Equipment: Infinity Delta Vulnerabilities: Improper Input Validation, Information Exposure Through Log Files, Improper Privilege Management 2. RISK EVALUATION Successful exploitation of these vulnerabilities could cause information disclosure of device logs, denial…










Stay connected