Schneider Electric Security Notification12-Easergy T200 Multiple Vulnerabilities
12 March 2024OverviewSchneider Electric is aware of multiple vulnerabilities in its Easergy T200 products.The Easergy T200 RTU Product Line (T200I, T200E, T200P) is a modular platform for mediumvoltage and low voltage public distribution network management. Note, this product has beenobsoleted since December 31st, 2021, and…
Exploited Solar Power Product Vulnerability Could Expose Energy Organizations to Attacks
Exploited Solar Power Product Vulnerability Could Expose Energy Organizations to Attacks: An actively exploited vulnerability in Contec’s SolarView solar power monitoring product poses a significant threat to energy organizations, potentially exposing them to attacks. This news item highlights the vulnerability, its impact on the affected organizations,…
Schneider Electric Security Notification Trio™ Licensed and License-free Data RadiosSchneider Electric Security Notification
12 December 2023 (9 April 2024) Overview Schneider Electric is aware of multiple vulnerabilities in its Trio Licensed and License-Free DataRadio products.The Trio Licensed Radio products are designed to provide complete, versatile, and highavailability system solutions for long range wireless data communications in SCADA and…
Schneider Electric Security Notification Easergy Studio Vulnerability
9 April 2024 OverviewSchneider Electric is aware of a vulnerability in its Easergy Studio product.The Easergy Studio product is a software solution for configuring, monitoring, and managingcontrol devices.Failure to apply the provided remediation below may risk unquoted search paths, which couldresult in escalation of privilege….
B&R Automation RuntimeFTP uses unsecure encryption mechanismsCVE ID: CVE-2024-0323/2024-02-05
Notice The information in this document is subject to change without notice, and should not be construed as a commitment by B&R. B&R provides no warranty, express or implied, including warranties of merchantability and fitness for a particular purpose, for the information contained in this…
AC500 V3Multiple DoS vulnerabilities – 2024-01-10
CVE-2022-47391, CVE-2023-37545,CVE-2023-37546, CVE-2023-37547,CVE-2023-37548, CVE-2023-37549,CVE-2023-37550, CVE-2023-37551,CVE-2023-37552, CVE-2023-37553,CVE-2023-37554, CVE-2023-37555,CVE-2023-37556, CVE-2023-37557,CVE-2023-37558, CVE-2023-37559 Notice The information in this document is subject to change without notice, and should not be construed as a commitment by ABB. ABB provides no warranty, express or implied, including warranties of merchantability and fitness for…
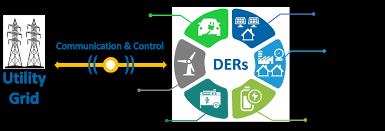
Distributed Energy Resources Cybersecurity Outlook:Vulnerabilities, Attacks, Impacts, and Mitigations
Abstract—The digitization and decentralization of the electric power grid are key thrusts for an economically and environmentally sustainable future. Towards this goal, distributed energy resources (DER), including rooftop solar panels, battery storage, electric vehicles, etc., are becoming ubiquitous in power systems. Power utilities benefit from…
POWER OUT?
SOLARINVERTERS AND THESILENT CYBER THREAT What’s the problem? As Australia accelerates adoption of renewable energy sources, new cyber securityvulnerabilities are being introduced through Internet of Things (IoT) devices. Cyber securityconcerns about these devices, notably photovoltaic inverters (solar inverters), have recentlycome to the fore, and policy…
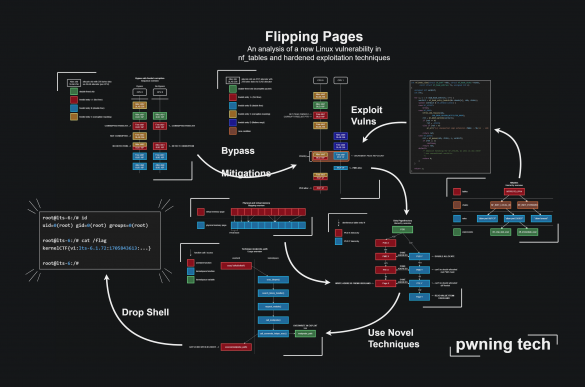
Flipping Pages: An analysis of a new Linux vulnerability in nf_tables and hardened exploitation techniques-Part II
4. Techniques 4.1. Page refcount juggling The first technique required for the exploit is juggling page refcounts. When we attempt to double-free a page in the kernel using the dedicated API functions, the kernel will check the refcount of the page: Codeblock 4.1.1: C code…
Flipping Pages: An analysis of a new Linux vulnerability in nf_tables and hardened exploitation techniques
This blogpost is the next instalment of my series of hands-on no-boilerplate vulnerability research blogposts, intended for time-travellers in the future who want to do Linux kernel vulnerability research. Specifically, I hope beginners will learn from my VR workflow and the seasoned researchers will learn…







Stay connected