OSIsoft PI Web API 2019
1. EXECUTIVE SUMMARY CVSS v3 7.7 ATTENTION: Exploitable remotely Vendor: OSIsoft Equipment: PI Web API 2019 Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote authenticated attacker with write access to a PI Server to trick a user into interacting with a PI…
Rockwell Automation FactoryTalk Linx Software
1. EXECUTIVE SUMMARY CVSS v3 9.6 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: FactoryTalk Linx Software Vulnerabilities: Improper Input Validation, Path Traversal, Unrestricted Upload of File with Dangerous Type 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to cause a denial-of-service…
Mitsubishi Electric MELSEC iQ-R series (Update A)
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Mitsubishi Electric Equipment: MELSEC iQ-R series Vulnerability: Resource Exhaustion 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled “ICSA-20-161-02 Mitsubishi Electric MELSEC iQ-R series” that was published June 9, 2020…
Siemens LOGO!
1. EXECUTIVE SUMMARY CVSS v3 9.4 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: LOGO! Vulnerability: Missing Authentication for Critical Function 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to read and modify device configurations and obtain project files from affected devices. 3….
Siemens SIMATIC, SINAMICS, SINEC, SINEMA, SINUMERIK
1. EXECUTIVE SUMMARY CVSS v3 6.7 ATTENTION: Low skill level to exploit Vendor: Siemens Equipment: SIMATIC, SINAMICS, SINEC, SINEMA, SINUMERIK Vulnerability: Unquoted Search Path or Element 2. RISK EVALUATION Successful exploitation of this vulnerability could allow authorized local users with administrative privileges to execute custom code with SYSTEM level…
Siemens SINUMERIK
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SINUMERIK Vulnerabilities: Buffer Underflow, Heap-based Buffer Overflow, Improper Initialization, Out-of-bounds Read, Stack-based Buffer Overflow, Access of Memory Location After End of Buffer, Off-by-one Error, Improper Null Termination, Improper Initialization 2. RISK EVALUATION Successful…
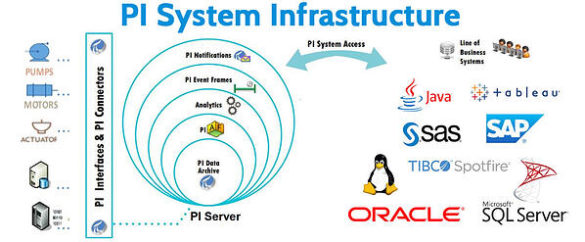
OSIsoft PI System (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: OSIsoft Equipment: PI System Vulnerabilities: Uncontrolled Search Path Element, Improper Verification of Cryptographic Signature, Incorrect Default Permissions, Uncaught Exception, Null Pointer Dereference, Improper Input Validation, Cross-site Scripting, Insertion of Sensitive Information into Log File 2….
Siemens Industrial Products (Update G)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Industrial Products ——— Begin Update G Part 1 of 4 ——— Vulnerabilities: Excessive Data Query Operations in a Large Data Table, Integer Overflow or Wraparound, Uncontrolled Resource Consumption ——— End Update G…
Siemens SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM (Update H)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM Vulnerability: Out-of-bounds Read 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-19-099-06 Siemens SIMATIC, SIMOCODE, SINAMICS, SITOP, and TIM (Update G)…
Medtronic Conexus Radio Frequency Telemetry Protocol (Update B)
1. EXECUTIVE SUMMARY CVSS v3 9.3 ATTENTION: Exploitable with adjacent access/low skill level to exploit Vendor: Medtronic Equipment: MyCareLink Monitor, CareLink Monitor, CareLink 2090 Programmer, specific Medtronic implanted cardiac devices listed below Vulnerabilities: Improper Access Control, Cleartext Transmission of Sensitive Information 2. UPDATE INFORMATION This updated advisory is a…










Stay connected