Schneider Electric EcoStruxure Operator Terminal Expert
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Low skill level to exploit/public exploits are available Vendor: Schneider Electric Equipment: EcoStruxure Operator Terminal Expert Vulnerabilities: SQL Injection, Path Traversal, Argument Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow unauthorized write access or remote code execution. 3. TECHNICAL…
Rockwell Automation EDS Subsystem
1. EXECUTIVE SUMMARY CVSS v3 8.2 ATTENTION: Exploitable from adjacent network/low skill level to exploit Vendor: Rockwell Automation Equipment: EDS Subsystem Vulnerabilities: Improper Restriction of Operations within the Bounds of a Memory Buffer, SQL Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities could lead to a denial-of-service condition….
Emerson OpenEnterprise
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Emerson Equipment: OpenEnterprise SCADA Software Vulnerabilities: Missing Authentication for Critical Function, Improper Ownership Management, Inadequate Encryption Strength 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker access to OpenEnterprise configuration services or…
Opto 22 SoftPAC Project
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Opto 22 Equipment: SoftPAC Project Vulnerabilities: External Control of File Name or Path, Improper Verification of Cryptographic Signature, Improper Access Control, Uncontrolled Search Path Element, Improper Authorization 2. RISK EVALUATION Successful exploitation of these vulnerabilities…
Eaton Intelligent Power Manager
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Eaton Equipment: Intelligent Power Manager Vulnerabilities: Improper Input Validation, Incorrect Privilege Assignment 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to perform command injection or code execution and allow non-administrator users…
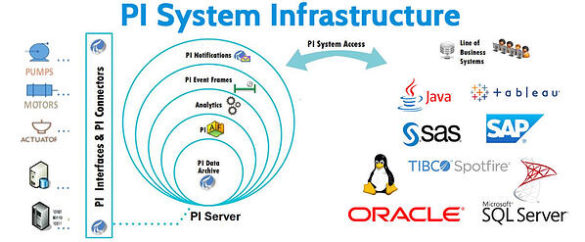
OSIsoft PI System
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: OSIsoft Equipment: PI System Vulnerabilities: Uncontrolled Search Path Element, Improper Verification of Cryptographic Signature, Incorrect Default Permissions, Uncaught Exception, Null Pointer Dereference, Improper Input Validation, Cross-site Scripting, Insertion of Sensitive Information into Log File 2….
Siemens KTK, SIDOOR, SIMATIC, and SINAMICS (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: KTK, SIDOOR, SIMATIC, and SINAMICS Vulnerability: Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-105-08 Siemens KTK, SIDOOR, SIMATIC, and SINAMICS that was published…
Siemens SIMATIC PCS 7, SIMATIC WinCC, and SIMATIC NET PC (Update C)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC PCS 7, SIMATIC WinCC, SIMATIC NET PC Vulnerability: Incorrect Calculation of Buffer Size 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled 20-042-06 Siemens SIMATIC PCS 7,…
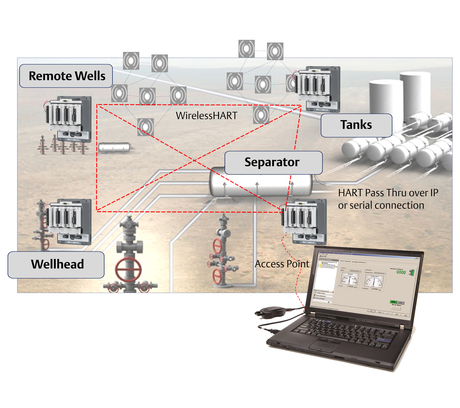
Emerson WirelessHART Gateway
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Emerson Equipment: Emerson WirelessHART Gateways (1410, 1420 and 1552WU) Vulnerability: Improper Access Control 2. RISK EVALUATION Successful exploitation of this vulnerability could disable the internal gateway firewall. Once the gateway’s firewall is disabled, a malicious…
3S-Smart Software Solutions GmbH CODESYS V3 Library Manager (Update A)
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Low skill level to exploit Vendor: 3S-Smart Software Solutions GmbH Equipment: CODESYS V3 Library Manager Vulnerability: Cross-site Scripting 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-19-255-02 3S-Smart Software Solutions GmbH CODESYS V3 Library Manager that…








Stay connected