Siemens Mendix Applications
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation requires to guess the identification of a target role which contains the elevated access rights. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following Siemens products, are affected: 3.2 Vulnerability Overview 3.2.1 IMPROPER PRIVILEGE MANAGEMENT CWE-269 Affected applications could…
ANSI Escape Injection Vulnerability in WinRAR
On 28 February 2024, RARLAB released an update for WinRAR, patching an ANSI escape sequence injection vulnerability that I had found in the console versions of RAR and UnRAR, affecting versions 6.24 and earlier. This vulnerability, tracked as CVE-2024–33899 for Linux and Unix systems and…
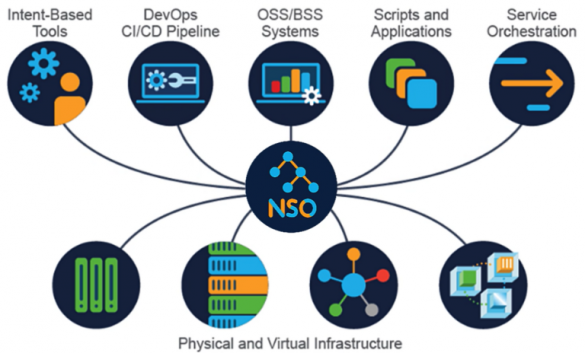
Cisco Crosswork Network Services Orchestrator Vulnerabilities
Summary Multiple vulnerabilities in the Cisco Crosswork Network Services Orchestrator (NSO) CLI could allow an authenticated, low-privileged, local attacker to read and write arbitrary files as root or elevate privileges to root on the underlying operating system. For more information about these vulnerabilities, see the Details section of this advisory.Cisco has…
SECURITY – Denial of Service Vulnerability in Control API ‘VPNI’, impact on S+ Operations, S+Engineering and S+ AnalystCVE ID: CVE-2024-0335
NoticeThe information in this document is subject to change without notice, and should not be construed as a commitment by ABB.ABB provides no warranty, express or implied, including warranties of merchantability and fitness for a particular purpose, for the information contained in this document, and…
Schneider Electric Security Notification12-Easergy T200 Multiple Vulnerabilities
12 March 2024OverviewSchneider Electric is aware of multiple vulnerabilities in its Easergy T200 products.The Easergy T200 RTU Product Line (T200I, T200E, T200P) is a modular platform for mediumvoltage and low voltage public distribution network management. Note, this product has beenobsoleted since December 31st, 2021, and…
Exploited Solar Power Product Vulnerability Could Expose Energy Organizations to Attacks
Exploited Solar Power Product Vulnerability Could Expose Energy Organizations to Attacks: An actively exploited vulnerability in Contec’s SolarView solar power monitoring product poses a significant threat to energy organizations, potentially exposing them to attacks. This news item highlights the vulnerability, its impact on the affected organizations,…
Schneider Electric Security Notification Trio™ Licensed and License-free Data RadiosSchneider Electric Security Notification
12 December 2023 (9 April 2024) Overview Schneider Electric is aware of multiple vulnerabilities in its Trio Licensed and License-Free DataRadio products.The Trio Licensed Radio products are designed to provide complete, versatile, and highavailability system solutions for long range wireless data communications in SCADA and…
Schneider Electric Security Notification Easergy Studio Vulnerability
9 April 2024 OverviewSchneider Electric is aware of a vulnerability in its Easergy Studio product.The Easergy Studio product is a software solution for configuring, monitoring, and managingcontrol devices.Failure to apply the provided remediation below may risk unquoted search paths, which couldresult in escalation of privilege….
B&R Automation RuntimeFTP uses unsecure encryption mechanismsCVE ID: CVE-2024-0323/2024-02-05
Notice The information in this document is subject to change without notice, and should not be construed as a commitment by B&R. B&R provides no warranty, express or implied, including warranties of merchantability and fitness for a particular purpose, for the information contained in this…
AC500 V3Multiple DoS vulnerabilities – 2024-01-10
CVE-2022-47391, CVE-2023-37545,CVE-2023-37546, CVE-2023-37547,CVE-2023-37548, CVE-2023-37549,CVE-2023-37550, CVE-2023-37551,CVE-2023-37552, CVE-2023-37553,CVE-2023-37554, CVE-2023-37555,CVE-2023-37556, CVE-2023-37557,CVE-2023-37558, CVE-2023-37559 Notice The information in this document is subject to change without notice, and should not be construed as a commitment by ABB. ABB provides no warranty, express or implied, including warranties of merchantability and fitness for…








Stay connected