NFC RELAY ATTACK ON TESLA MODEL Y
This paper will walk you through the proof-of-concept and technical details of exploitation forIOActive’s recent NFC relay attack on the newest Tesla vehicle, the Model Y.To successfully carry out the attack, IOActive reverse-engineered the NFC protocol Tesla usesbetween the NFC card and the vehicle, and…
Cisco NX-OS Software MPLS Encapsulated IPv6 Denial of Service Vulnerability
Summary A vulnerability with the handling of MPLS traffic for Cisco NX-OS Software could allow an unauthenticated, remote attacker to cause the netstack process to unexpectedly restart, which could cause the device to stop processing network traffic or to reload. This vulnerability is due to…
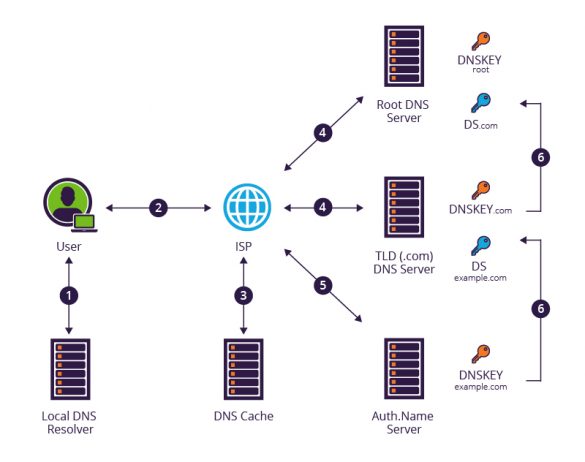
The KeyTrap Denial-of-Service Algorithmic Complexity Attacks on DNSVersion: January 2024
Abstract—Availability is a major concern in the design of DNSSEC. To ensure availability, DNSSEC follows Postel’s Law [RFC1122]: ”Be liberal in what you accept, and conservative inwhat you send.” Hence, nameservers should send not just one matching key for a record set, but all the…
New WiFi Authentication Vulnerabilities Discovered
One vulnerability affects Android, ChromeOS and Linux devices connecting to enterprise WiFi networks, another affects home WiFi using a Linux device as a wireless access point. Two new vulnerabilities in open-source WiFi software allow attackers to trick victims into connecting to malicious clones of trusted…
Siemens Parasolid
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to leverage the vulnerability to perform remote code execution in the context of the current process. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following products of Siemens are affected: 3.2…
CVE-2023-50387: KeyTrap – Extreme CPU consumption in DNSSEC validator
CVE: CVE-2023-50387 Title: KeyTrap – Extreme CPU consumption in DNSSEC validator Document version: 2.0 Posting date: 13 February 2024 Program impacted: BIND 9 Versions affected: BIND (Versions prior to 9.11.37 were not assessed.) BIND Supported Preview Edition (Versions prior to 9.11.37-S1 were not assessed.) Severity: High Exploitable: Remotely Description: The processing of…
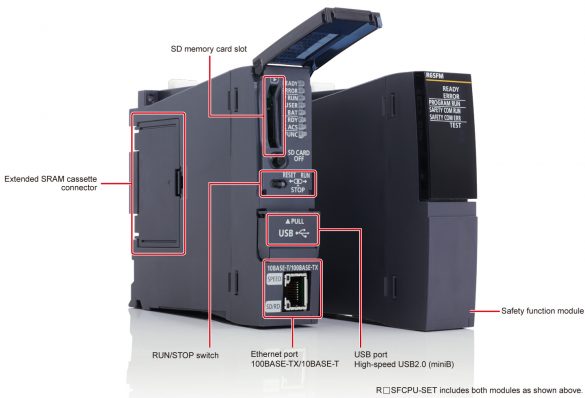
Mitsubishi Electric MELSEC iQ-R Series Safety CPU
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a non-administrator user to disclose the credentials (user ID and password) of a user with a lower access level than themselves. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Mitsubishi Electric reports that the…
Cisco Expressway Series Cross-Site Request Forgery Vulnerabilities
Summary Affected Products Details The vulnerabilities are not dependent on one another. Exploitation of one of the vulnerabilities is not required to exploit another vulnerability. In addition, a software release that is affected by one of the vulnerabilities may not be affected by the other…
glibc qsort() Out-Of-Bounds Read / Write
Summary We discovered a memory corruption in the glibc’s qsort() function, due to a missing bounds check. To be vulnerable, a program must call qsort() with a nontransitive comparison function (a function cmp(int a, int b) that returns (a – b), for example) and with…
Heap-based buffer overflow in the glibc’s syslog ()
Summary -Heap-based buffer overflow in the glibc’s syslog () We discovered a heap-based buffer overflow in the GNU C Library’s __vsyslog_internal() function, which is called by both syslog() and vsyslog(). This vulnerability was introduced in glibc 2.37 (in August 2022) by the following commit: https://sourceware.org/git?p=glibc.git;a=commit;h=52a5be0df411ef3ff45c10c7c308cb92993d15b1…









Stay connected