Experts found 36 vulnerabilities in the LTE protocol
A team of researchers from the Korea Advanced Institute of Science and Technology Constitution (KAIST) discovered 36 vulnerabilities in the LTE protocol. Security experts from the Korea Advanced Institute of Science and Technology Constitution (KAIST) have discovered 36 vulnerabilities in the LTE protocol used by most…
ENTTEC Lighting Controllers
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: ENTTEC Equipment: Datagate MK2, Storm 24, Pixelator Vulnerability: Missing Authentication for Critical Function 2. RISK EVALUATION Successful exploitation of this vulnerability could reboot this device allowing a continual denial of service condition. 3. TECHNICAL DETAILS…
PHOENIX CONTACT RAD-80211-XD
1. EXECUTIVE SUMMARY CVSS v3 9.9 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Phoenix Contact Equipment: RAD-80211-XD Vulnerability: Command Injection 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to execute system level commands with administrative privileges. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS According to…
Siemens SCALANCE X
1. EXECUTIVE SUMMARY CVSS v3 5.4 ATTENTION: Exploitable remotely Vendor: Siemens Equipment: SCALANCE X Vulnerability: Expected Behavior Violation 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to feed data over a mirror port and into the mirrored network. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The…
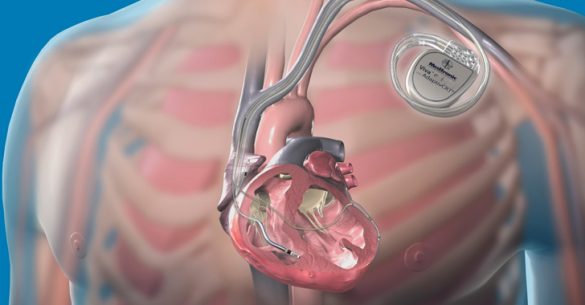
Medtronic’s Implantable Defibrillators Vulnerable to Life-Threatening Hacks
The U.S. Department of Homeland Security Thursday issued an advisory warning people of severe vulnerabilities in over a dozen heart defibrillators that could allow attackers to fully hijack them remotely, potentially putting lives of millions of patients at risk. Cardioverter Defibrillator is a small surgically…
Medtronic Conexus Radio Frequency Telemetry Protocol
. EXECUTIVE SUMMARY CVSS v9.3 ATTENTION: Exploitable with adjacent access/low skill level to exploit Vendor: Medtronic Equipment: MyCareLink Monitor, CareLink Monitor, CareLink 2090 Programmer, specific Medtronic implanted cardiac devices listed below Vulnerabilities: Improper Access Control, Cleartext Transmission of Sensitive Information 2. RISK EVALUATION Successful exploitation of these vulnerabilities may…
Columbia Weather Systems MicroServer
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Columbia Weather Systems, Inc. Equipment: Weather MicroServer Vulnerabilities: Cross-site Scripting, Path Traversal, Improper Authentication, Improper Input Validation, Code Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow disclosure of data, cause a denial-of-service…
AVEVA InduSoft Web Studio and InTouch Edge HMI
1. EXECUTIVE SUMMARY CVSS v3 6.5 ATTENTION: Low skill level to exploit Vendor: AVEVA Equipment: InduSoft Web Studio, InTouch Edge HMI Vulnerability: Uncontrolled Search Path Element 2. RISK EVALUATION Successful exploitation of this vulnerability could allow execution of unauthorized code or commands. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The…
LCDS – Leão Consultoria e Desenvolvimento de Sistemas Ltda ME LAquis SCADA ELS Files
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: LCDS—Leão Consultoria e Desenvolvimento de Sistemas LTDA ME Equipment: LAquis SCADA Vulnerability: Out-of-Bounds Write 2. RISK EVALUATION Successful exploitation of this vulnerability could allow remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following version…
Gemalto Sentinel UltraPro
1. EXECUTIVE SUMMARY CVSS v3 6.5 ATTENTION: Low skill level to exploit Vendor: Gemalto Equipment: Sentinel UltraPro Vulnerability: Uncontrolled Search Path Element 2. RISK EVALUATION Successful exploitation of this vulnerability could allow execution of unauthorized code or commands. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of Sentinel…









Stay connected