Equinox Control Expert
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Equinox Equipment: Control Expert Vulnerability: Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) 2. RISK EVALUATION Successful exploitation of this vulnerability may allow remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED…
Reliable Controls MACH-ProWebCom/Sys
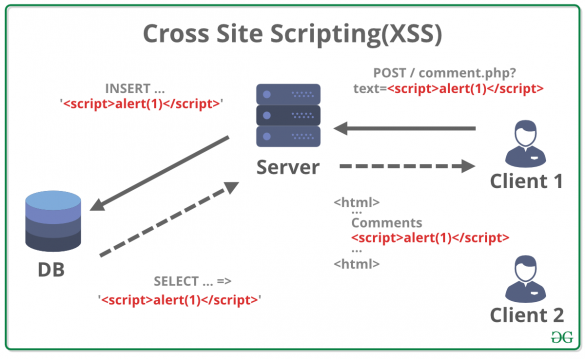
1. Reliable Controls MACH-ProWebCom/Sys EXECUTIVE SUMMARY CVSS v3 8.2 ATTENTION: Exploitable remotely Vendor: Reliable Controls Equipment: MACH-ProWebCom/Sys Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to execute commands on behalf of the affected user. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following…
AVEVA Vijeo Citect and Citect SCADA (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit ——— Begin Update A Part 1 of 5 ——— Vendor: AVEVA and Schneider Electric Equipment: AVEVA’s Vijeo Citect and Citect SCADA; Schneider Electric’s Power SCADA Operation ——— End Update A Part 1 of 5 ———…
Philips IntelliBridge EC40/80 (Update A)
1. EXECUTIVE SUMMARY CVSS v3 6.3 ATTENTION: Low skill level to exploit Vendor: Philips Equipment: IntelliBridge EC40 and EC80 Vulnerability: Inadequate Encryption Strength 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSMA-19-318-01 Philips IntelliBridge EC40/80 that was published November 14, 2019, on the…
Siemens SPPA-T3000
1. Siemens SPPA-T3000-EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SPPA-T3000 Vulnerabilities: Improper Authentication, Cleartext Transmission of Sensitive Information, Unrestricted Upload of File with Dangerous Type, Heap-based Buffer Overflow, Integer Overflow or Wraparound, Out-of-bounds Read, Improper Access Control, Stack-based Buffer Overflow, SFP…
GE S2020/S2020G Fast Switch 61850
1. EXECUTIVE SUMMARY CVSS v3 4.6 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: GE Equipment: GE S2020/S2020G Fast Switch 61850 Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability may allow an attacker to inject arbitrary code and allow disclosure of sensitive data. 3. TECHNICAL DETAILS…
Siemens SiNVR 3
1. EXECUTIVE SUMMARY CVSS v3 9.9 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SiNVR 3 Vulnerabilities: Cleartext Storage of Sensitive Information in GUI, Improper Authentication, Relative Path Traversal, Missing Authentication for Critical Function, Weak Cryptography for Passwords, Exposed Dangerous Method or Function 2. RISK EVALUATION Successful…
PLC Cycle Time Influences (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available Vendors: ABB, Phoenix Contact, Schneider Electric, Siemens, WAGO Equipment: Programmable Logic Controllers Vulnerability: Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-19-106-03 PLC Cycle…
Siemens XHQ Operations Intelligence
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: XHQ Operations Intelligence Vulnerabilities: Cross-site Request Forgery, Improper Neutralization of Script-Related HTML Tags in a Web Page, Improper Input Validation 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to…
Siemens EN100 Ethernet Module
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: EN100 Ethernet Module Vulnerabilities: Improper Restriction of Operations within the Bounds of a Memory Buffer, Cross-site Scripting, Relative Path Traversal 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to…







Stay connected