High severity XML external entity flaw affects Sauter building automation product
A security researcher has found a serious vulnerability in a building automation product from Sauter AG that could be exploited to steal files from an affected system. Sauter AG CASE Suit is a building automation product used worldwide that is affected by a high severity XML external entity (XXE)…
New attack by Anonymous Italy: personal data from ministries and police have been released online
New attack by Anonymous Italy: personal data from ministries and police have been released online. The site of Fratelli d’Italia, a post-fascist party, has been defaced The iconoclastic fury of Italian Anonymous does not stop. As announced, the three groups that coordinate the operation “Black Week”…
Flaws in Popular Self-Encrypting SSDs Let Attackers Decrypt Data
We all have something to hide, something to protect. But if you are also relying on self-encrypting drives for that, then you should read this news carefully. Security researchers have discovered multiple critical vulnerabilities in some of the popular self-encrypting solid state drives (SSD) that…
Two New Bluetooth Chip Flaws Expose Millions of Devices to Remote Attacks
Security researchers have unveiled details of two critical vulnerabilities in Bluetooth Low Energy (BLE) chips embedded in millions of access points and networking devices used by enterprises around the world. Dubbed BleedingBit, the set of two vulnerabilities could allow remote attackers to execute arbitrary code and…
Rockwell Automation Stratix 5100 (Update A)
1. EXECUTIVE SUMMARY CVSS v3 6.9 ATTENTION: Exploitable remotely/public exploits are available Vendor: Rockwell Automation Equipment: Stratix 5100 Wireless Access Point/Workgroup Bridge Vulnerability: Reusing a Nonce 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled “ICSA-17-299-02 Rockwell Automation Stratix 5100” that was published October…
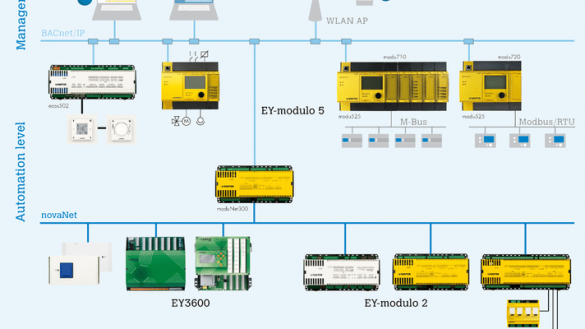
Fr. Sauter AG CASE Suite
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Fr. Sauter AG Equipment: CASE Suite Vulnerability: Improper Restriction of XML External Entity Reference 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to remotely retrieve unauthorized files from the system. 3….
Circontrol CirCarLife
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Circontrol Equipment: CirCarLife Vulnerabilities: Authentication Bypass Using an Alternate Path or Channel, Insufficiently Protected Credentials 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow a remote attacker to retrieve credentials stored in clear text…
AVEVA InduSoft Web Studio and InTouch Edge HMI (formerly InTouch Machine Edition)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: AVEVA Software, LLC. (AVEVA) Equipment: InduSoft Web Studio and InTouch Edge HMI (formerly InTouch Machine Edition) Vulnerabilities: Stack-based Buffer Overflow, Empty Password in Configuration File 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow…
Schneider Electric Software Update (SESU)
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Schneider Electric Equipment: Software Update (SESU) Vulnerability: DLL hijacking 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-18-305-02 Schneider Electric Software Update that was published November 1, 2018, on the…
Unpatched MS Word Flaw Could Allow Hackers to Infect Your Computer
Cybersecurity researchers have revealed an unpatched logical flaw in Microsoft Office 2016 and older versions that could allow an attacker to embed malicious code inside a document file, tricking users into running malware onto their computers. Discovered by researchers at Cymulate, the bug abuses the…










Stay connected