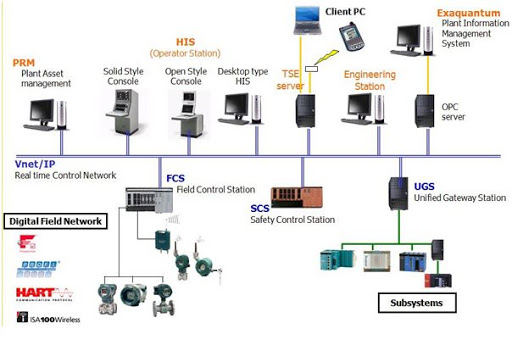
Yokogawa CENTUM
1. EXECUTIVE SUMMARY CVSS v3 8.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Yokogawa Equipment: CENTUM Vulnerabilities: Improper Authentication, Path Traversal 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow a remote unauthenticated attacker to send tampered communication packets or create/overwrite any file and run any commands….
Tridium Niagara
1. EXECUTIVE SUMMARY CVSS v3 4,3 ATTENTION: Exploitable from adjacent network/low skill level to exploit Vendor: Tridium Equipment: Niagara Vulnerability: Synchronous Access of Remote Resource without Timeout 2. RISK EVALUATION Successful exploitation of this vulnerability could result in a denial-of-service condition. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following…
Siemens SCALANCE, RUGGEDCOM
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SCALANCE, RUGGEDCOM Vulnerability: Classic Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to gain unauthenticated access to a device and cause a buffer overflow to execute custom…
Siemens SIMATIC, SIMOTICS
1. EXECUTIVE SUMMARY CVSS v3 3.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC, SIMOTICS Vulnerability: TOCTOU Race Condition 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to read a discrete set of traffic over the air after a Wi-Fi device state…
Siemens Desigo CC
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Desigo CC Vulnerability: Code Injection 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to gain remote code execution on the server with SYSTEM privileges. 3. TECHNICAL DETAILS 3.1…
Siemens Automation License Manager
1. EXECUTIVE SUMMARY CVSS v3 7.3 ATTENTION: Low skill level to exploit Vendor: Siemens Equipment: Automation License Manager (ALM) Vulnerability: Improper Authorization 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to locally escalate privileges and modify files that should be protected against writing. 3. TECHNICAL…
Siemens SICAM A8000 RTUs
1. EXECUTIVE SUMMARY CVSS v3 8.3 ATTENTION: Exploitable remotely Vendor: Siemens Equipment: SICAM A8000 Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could compromise the confidentiality, integrity, and availability of the web application. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of SICAM A8000 RTUs…
Exploiting DLLs A guide to DLL Hijacking
Abstract As per the recent statistics available Windows still remains the most used operating system for digital devices. Almost 77% of the computers today run Windows operating system. With its GUI based implementation and ease of compatibility with most of the available software, Windows is…
SMB Enumeration & Exploitation & Hardening
IntroductionWhat is SMB?SMB (Server Message Block) is a network protocol for accessing files, printers and other deviceson the network. Server Message Block provides file sharing, network browsing, printing services,and interprocess communication over a network. Most usage of SMB involves computersrunning Microsoft Windows, where it was…
Siemens Opcenter Execution Core (Update A)
1. EXECUTIVE SUMMARY CVSS v3 8.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Opcenter Execution Core Vulnerabilities: Cross-site Scripting, SQL Injection, Improper Access Control 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-196-07 Siemens Opcenter Execution Core that was published…









Stay connected