Siemens UMC Stack
1. EXECUTIVE SUMMARY CVSS v3 6.7 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: UMC Stack Vulnerabilities: Unquoted Search Path or Element, Uncontrolled Resource Consumption, Improper Input Validation 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-196-05 Siemens UMC Stack that…
Siemens SIMATIC, SINAMICS, SINEC, SINEMA, SINUMERIK (Update B)
1. EXECUTIVE SUMMARY CVSS v3 6.7 ATTENTION: Low skill level to exploit Vendor: Siemens Equipment: SIMATIC, SINAMICS, SINEC, SINEMA, SINUMERIK Vulnerability: Unquoted Search Path or Element 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-161-04 Siemens SIMATIC, SINAMICS, SINEC, SINEMA, SINUMERIK (Update A)…
Bypass Certificate Pinning in modern Android application via custom Root CA
I. IntroductionThis document is intended to provide detailed instructions for bypass certificate pinning via custom Root CA. It covers all the required topics for understanding this method. The proof of concept will help visualize and perform bypass certificate pinning, specially in modern applications now and…
Siemens SCALANCE & SIMATIC (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SCALANCE, SIMATIC Vulnerability: Resource Exhaustion 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-105-07 Siemens SCALANCE & SIMATIC that was published April 14, 2020 on the ICS…
Cleanly Escaping the Chrome Sandbox
This post will explain how we discovered and exploited Issue 1062091, a use-after-free (UAF) in the browser process leading to a sandbox escape in Google Chrome as well as Chromium-based Edge. Background Our goal is to make this post accessible to those unfamiliar with Chrome exploitation,…
CVE 2020-6418 Type confusion in V8 in Google Chrome prior to 80.0.3987.122
CVE-2020-6418 is a type confusion vulnerability in V8, Google Chrome’s open-source JavaScriptand WebAssembly engine. Vulnerability Description On February 25, security updates were released for Google Chrome and Microsoft Edge. The opensource JavaScript and WebAssembly engines in V8 in Google Chrome before 80.0.3987.122 andMicrosoft Edge browser…
Siemens Industrial Products SNMP Vulnerabilities (Update B)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Various SCALANCE, SIMATIC, SIPLUS products Vulnerabilities: Data Processing Errors, NULL Pointer Dereference 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-20-042-02 Siemens Industrial Products SNMP Vulnerabilities (Update…
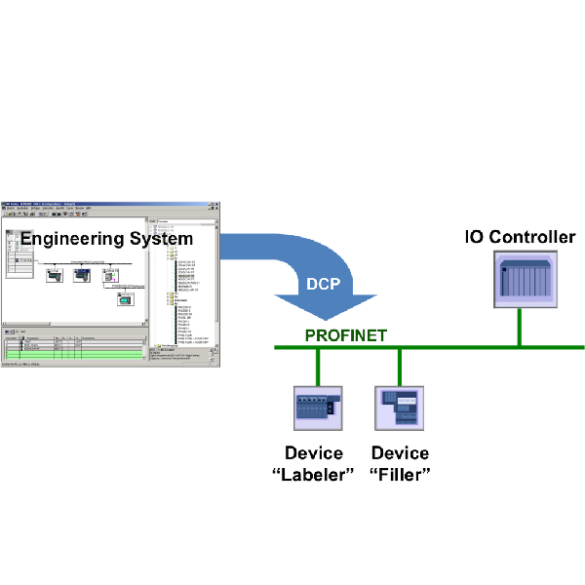
Siemens PROFINET-IO Stack (Update B)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Siemens PROFINET-IO Stack Vulnerability: Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-20-042-04 Siemens PROFINET-IO Stack (Update A) that was published March 10, 2020,…
Siemens Industrial Real-Time (IRT) Devices (Update D)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Industrial Real-Time (IRT) Devices Vulnerability: Improper Input Validation 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-19-283-01 Siemens Industrial Real-Time (IRT) Devices (Update C) that was published…
Siemens PROFINET Devices (Update G)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: PROFINET Devices Vulnerability: Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-19-283-02 Siemens PROFINET Devices (Update F) that was published July 14, 2020, to…









Stay connected