At least 1,300 Harbor cloud registry installs open to attack
A critical security flaw in Harbor cloud native registry for container images could be exploited to obtain admin privileges on a vulnerable hosting system. Palo Alto Networks’ Unit 42 researcher Aviv Sasson discovered a critical vulnerability in Harbor cloud native registry for container images. The flaw, tracked as CVE-2019-16097,…
Advantech WebAccess
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Advantech Equipment: WebAccess Vulnerabilities: Code Injection, Command Injection, Stack-based Buffer Overflow, Improper Authorization 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to execute arbitrary code, access files…
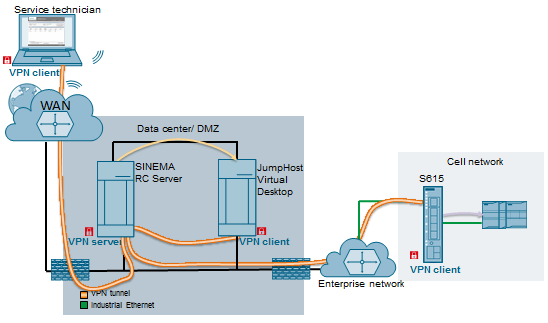
Siemens SINEMA Remote Connect Server
1. EXECUTIVE SUMMARY CVSS v3 8.1 ATTENTION: Exploitable remotely Vendor: Siemens Equipment: SINEMA Remote Connect Server Vulnerabilities: Improper Restriction of Excessive Authentication Attempts, Information Exposure, Cross-Site Request Forgery, Use of Password Hash with Insufficient Computational Effort 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow an attacker unauthorized…
Honeywell Performance IP Cameras and Performance NVRs
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Honeywell Equipment: Performance IP Cameras and Performance NVRs Vulnerability: Information Exposure 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to view device configuration information. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The…
Philips IntelliVue WLAN
1. EXECUTIVE SUMMARY CVSS v3 6.4 Vendor: Philips Equipment: IntelliVue M3002A X2 MMS Transport Monitor/Module and IntelliVue MP monitors (MP2/X2, MP5, MP20-MP90, MX600, MX700 and MX800) Vulnerabilities: Use of Hard-coded Password, Download of Code Without Integrity Check 2. RISK EVALUATION Successful exploitation of these vulnerabilities may cause corruption…
3S-Smart Software Solutions GmbH CODESYS V3 Web Server
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: 3S-Smart Software Solutions GmbH Equipment: CODESYS V3 web server Vulnerabilities: Path Traversal, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow an attacker to create a denial-of-service condition, to perform remote…
3S-Smart Software Solutions GmbH CODESYS V3 Products Containing a CODESYS Communication Server
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: 3S-Smart Software Solutions GmbH Equipment: CODESYS V3 products containing a CODESYS communication server Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could cause a denial-of-service condition. 3. TECHNICAL DETAILS 3.1 AFFECTED…
Mitsubishi Electric Europe B.V. smartRTU and INEA ME-RTU (Update A)
1 EXECUTIVE SUMMARY ——— Begin Update A ——— CISA is aware of a public report of vulnerabilities with proof-of-concept (PoC) exploit code affecting Mitsubishi Electric Europe B.V. smartRTU (Versions 2.02 and prior) and INEA ME-RTU (Versions 3.0 and prior), remote terminal unit products. According to…
Delta Electronics TPEditor
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Delta Electronics Equipment: TPEditor Vulnerabilities: Stack-based Buffer Overflow, Heap-based Buffer Overflow, Out-of-bounds Write 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow information disclosure, remote code execution, or may crash the application. 3. TECHNICAL DETAILS…
Siemens SINETPLAN
1. EXECUTIVE SUMMARY CVSS v3 8.0 ATTENTION: Low skill level to exploit Vendor: Siemens Equipment: Siemens Network Planner (SINETPLAN) Vulnerability: Improper Authorization 2. RISK EVALUATION Successful exploitation of this vulnerability could allow information disclosure, code execution, and denial-of-service. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of SINETPLAN,…








Stay connected