Cisco addresses a critical bug in ASR 9000 series Routers
Cisco released security patches for 30 vulnerabilities, including a critical flaw in ASR 9000 Series Aggregation Services Routers running IOS XR 64-bit. The critical vulnerability in ASR 9000 Series Aggregation Services Routers running IOS XR 64-bit is tracked as CVE-2019-1710 (CVSS score of 9.8). The…
Delta Industrial Automation CNCSoft
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Delta Electronics (Delta) Equipment: Delta Industrial Automation CNCSoft Vulnerabilities: Stack-based Buffer Overflow, Heap-based Buffer Overflow, Out-of-bounds Read 2. RISK EVALUATION Successful exploitation of these vulnerabilities could cause buffer overflow conditions that may allow information disclosure, remote…
WAGO Series 750-88x and 750-87x
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: WAGO Equipment: Series 750-88x and 750-87x Vulnerability: Use of Hard-coded Credentials 2. RISK EVALUATION This vulnerability allows a remote attacker to change the settings or alter the programming of the device. 3. TECHNICAL DETAILS 3.1…
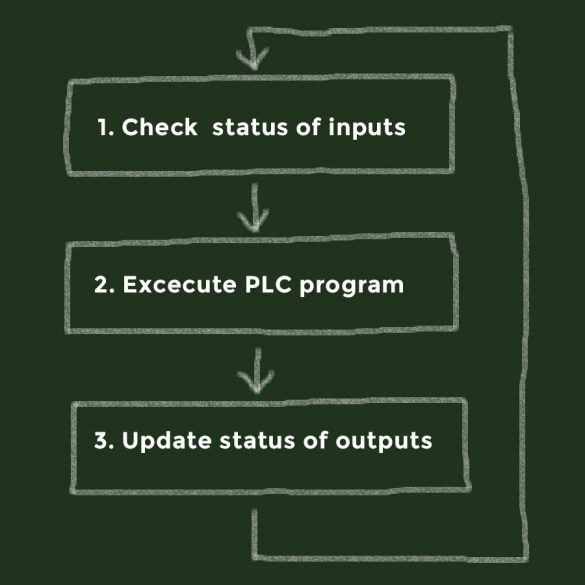
PLC Cycle Time Influences
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available Vendors: ABB, Phoenix Contact, Schneider Electric, Siemens, WAGO Equipment: Programmable Logic Controllers Vulnerability: Uncontrolled Resource Consumption 2. RISK EVALUATION High network load can consume CPU power in such a way that the normal…
CVE-2019-0803 Windows flaw exploited to deliver PowerShell Backdoor
A recently fixed local privilege escalation flaw in windows (CVE-2019-0803) had been exploited by bad actors to deliver PowerShell Backdoor. April 2019 Patch Tuesday security updates addressed a local privilege escalation flaw in Windows operating system, tracked as CVE-2019-0859 that had been exploited by threat actors…
MAR-10135536-8 – North Korean Trojan: HOPLIGHT
Summary Description This Malware Analysis Report (MAR) is the result of analytic efforts between Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI). Working with U.S. Government partners, DHS and FBI identified Trojan malware variants used by the North Korean government. This…
Siemens SIMOCODE pro V EIP
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMOCODE pro V EIP Vulnerability: Uncontrolled Resource Consumption 2. RISK EVALUATION Successful exploitation of this vulnerability could cause a denial-of-service condition. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of SIMOCODE…
Siemens Spectrum Power 4.7
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Spectrum Power 4.7 Vulnerability: Command Injection 2. RISK EVALUATION Successful exploitation of this vulnerability in versions of Spectrum Power 4 using the user-specific project enhancement (PE) Web Office Portal (WOP) are affected by…
Siemens Industrial Products with OPC UA
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC, SINEC-NMS, SINEMA, SINEMURIK Industrial Control Products with OPC UA Vulnerability: Uncaught Exception 2. RISK EVALUATION Successful exploitation of this vulnerability could cause a denial-of-service condition on the affected service or device. 3….
Siemens SINEMA Remote Connect
1. EXECUTIVE SUMMARY CVSS v3 8.3 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SINEMA Remote Connect (Client and Server) Vulnerabilities: Incorrect Calculation of Buffer Size, Out-of-bounds Read, Stack-based Buffer Overflow, Improper Handling of Insufficient Permissions 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an…








Stay connected