Schneider Electric Zelio Soft 2
. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Schneider Electric Equipment: Zelio Soft 2 Vulnerability: Use After Free 2. RISK EVALUATION Successful exploitation of this vulnerability could allow for remote code execution when opening a specially crafted project file. 3. TECHNICAL DETAILS 3.1 AFFECTED…
Schneider Electric Pro-face GP-Pro EX
EXECUTIVE SUMMARY CVSS v3 9.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Schneider Electric Equipment: Pro-face GP-Pro EX Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to modify code to launch an arbitrary executable upon launch of the program. 3….
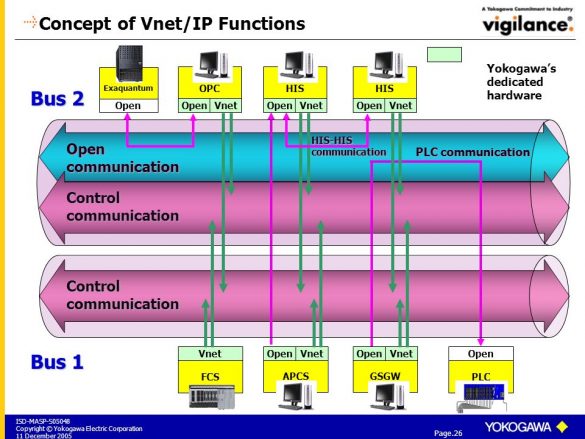
Yokogawa Vnet/IP Open Communication Driver
1. EXECUTIVE SUMMARY CVSS v7.5 ATTENTION: Exploitable remotely/Low skill level to exploit Vendor: Yokogawa Equipment: Vnet/IP Open Communication Driver Vulnerability: Resource Management Error 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to cause Vnet/IP network communications to controlled devices to become unavailable. 3. TECHNICAL DETAILS…
Hetronic Nova-M
1. EXECUTIVE SUMMARY CVSS v3 7.6 ATTENTION: Low skill level to exploit Vendor: Hetronic Equipment: Nova-M Vulnerability: Authentication Bypass by Capture-Replay 2. RISK EVALUATION Successful exploitation of this vulnerability could allow unauthorized users to view commands, replay commands, control the device, or stop the device from running. 3. TECHNICAL…
Experts disclosed an unpatched Kernel buffer overflow in Trusteer Rapport for MacOS
Researchers from Trustwave SpiderLabs discovered an unpatched kernel-level vulnerability in driver used by IBM Trusteer Rapport endpoint security tool. The issue affects endpoint security tool for MacOS, IBM released a patch but failed to address the vulnerability within the 120-day disclosure deadline. The IBM Trusteer…
Omron CX-Supervisor (Update A)
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Low skill level to exploit Vendor: Omron Equipment: CX-Supervisor Vulnerabilities: Stack-based Buffer Overflow, Use After Free, Access of Uninitialized Pointer, Double Free, Out-of-bounds Write, Untrusted Pointer Dereference, Heap-based Buffer Overflow. 2. UPDATE INFORMATION This updated advisory…
Rockwell Automation FactoryTalk Services Platform
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: FactoryTalk Services Platform Vulnerability: Heap-based Buffer Overflow 2. REPOSTED INFORMATION This advisory was originally posted to the HSIN ICS-CERT library on November 27, 2018, and is being released…
Schneider Electric EcoStruxure
. EXECUTIVE SUMMARY CVSS v3 7.4 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Schneider Electric Equipment: EcoStruxure Vulnerability: Open Redirect 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to use this device as a platform to conduct a phishing attack. 3. TECHNICAL DETAILS 3.1…
Horner Automation Cscape
Legal Notice All information products included in http://ics-cert.us-cert.gov are provided “as is” for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information contained within. DHS does not endorse any commercial product or service, referenced in this product…
Schneider Electric Triconex Tricon (Update B)
1. EXECUTIVE SUMMARY CVSS v3 9.0 ATTENTION: Exploitable remotely/HatMan malware specifically targets these vulnerabilities. Vendor: Schneider Electric Equipment: Triconex Tricon, Model 3008 Vulnerabilities: Improper Restriction of Operations within the Bounds of a Memory Buffer 2. UPDATE INFORMATION This updated advisory is a follow-up to the…








Stay connected