Siemens SCALANCE X200 IRT
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: SCALANCE X200 IRT Products Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could allow remote attackers to cause a denial-of-service condition. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following Siemens products…
VMware Releases Security Updates for Multiple products
VVMware has released security updates to address multiple vulnerabilities in multiple products. A remote attacker could exploit some of these vulnerabilities to take control of an affected system. VMSA-2022-0031 1. Impacted Products VMware vRealize Network Insight (vRNI) 2. Introduction Multiple vulnerabilities in VMware vRealize Network Insight…
Fortinet Releases Security Updates for FortiOS
Fortinet has released security updates to address a heap-based buffer overflow vulnerability (CVE-2022-42475) in FortiOS. An attacker could exploit this vulnerability to take control of an affected system. FortiOS – heap-based buffer overflow in sslvpnd Summary A heap-based buffer overflow vulnerability [CWE-122] in FortiOS SSL-VPN may…
Cisco Releases Security Advisory for IP Phone 7800 and 8800 Series
Summary A vulnerability in the Cisco Discovery Protocol processing feature of Cisco IP Phone 7800 and 8800 Series firmware could allow an unauthenticated, adjacent attacker to cause a stack overflow on an affected device.This vulnerability is due to insufficient input validation of received Cisco Discovery…
CISA Releases Phishing Infographic
CISA published a Phishing Infographic to help protect both organizations and individuals from successful phishing operations. This infographic provides a visual summary of how threat actors execute successful phishing operations. Details include metrics that compare the likelihood of certain types of “bait” and how commonly…
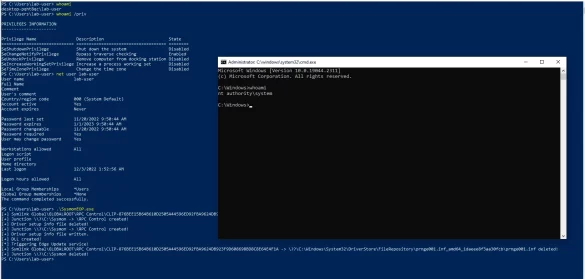
CVE-2022-41120 PoC released for Windows Sysmon Elevation of Privilege Vulnerability
A security researcher has published details and proof-of-concept (PoC) code for a Microsoft Windows Sysmon vulnerability that could be exploited to gain elevated privileges on the system. Tracked as CVE-2022-41120 (CVSS score of 7.8), the security defect was identified and reported in June, with a…
Mitsubishi Electric MELSEC iQ-R Series
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low attack complexity Vendor: Mitsubishi Electric Equipment: MELSEC iQ-R Series Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote unauthenticated attacker to cause a denial-of-service condition on a target product by sending specially crafted…
Mitsubishi Electric GT SoftGOT2000
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Mitsubishi Electric Corporation Equipment: GT SoftGOT2000 Vulnerability: Operating System (OS) Command Injection 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to execute malicious OS commands. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Mitsubishi Electric…
Cradlepoint IBR600
1. EXECUTIVE SUMMARY CVSS v3 7.1 ATTENTION: Low attack complexity Vendor: Cradlepoint Equipment: IBR600 Vulnerabilities: Command Injection 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to execute code and native system commands. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of Cradlepoint IBR600 are…
Cisco Identity Services Engine Cross-Site Scripting Vulnerability
A vulnerability in the External RESTful Services (ERS) API of Cisco Identity Services Engine (ISE) Software could allow an authenticated, remote attacker to conduct a cross-site scripting (XSS) attack against a user of the interface of an affected device. This vulnerability is due to insufficient…










Stay connected