PTC Kepware KEPServerEX (Update A)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: PTC Equipment: Kepware KEPServerEX Vulnerabilities: Stack-based Buffer Overflow, Heap-based Buffer Overflow, Use After Free 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-352-02 PTC Kepware KEPServerEX that was published…
ARC Informatique PcVue (Update A)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: ARC Informatique Equipment: PcVue Vulnerabilities: Deserialization of Untrusted Data, Access to Critical Private Variable via Public Method, Information Exposure of Sensitive Information to an Unauthorized Actor 2. UPDATE INFORMATION This updated advisory is a follow-up…
Johnson Controls Sensormatic Electronics American Dynamics victor Web Client and Software House C•CURE Web Client (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.1 ATTENTION: Low skill level to exploit Vendor: Sensormatic Electronics, LLC, a subsidiary of Johnson Controls Equipment: American Dynamics victor Web Client Vulnerability: Improper Authorization 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-282-01…
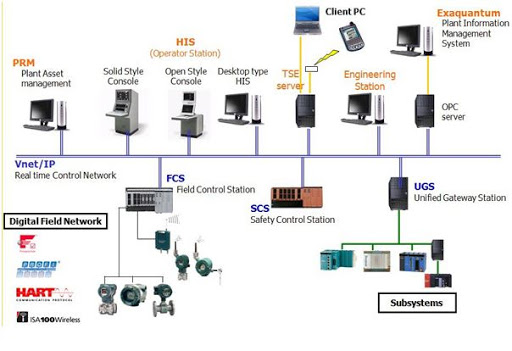
Yokogawa CENTUM (Update A)
1. EXECUTIVE SUMMARY CVSS v3 8.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Yokogawa Equipment: CENTUM Vulnerabilities: Improper Authentication, Path Traversal 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-224-01 Yokogawa CENTUM that was published August 11, 2020, on the ICS webpage…
Mitsubishi Electric Multiple Factory Automation Engineering Software Products (Update A)
1. EXECUTIVE SUMMARY CVSS v3 8.3 ATTENTION: Exploitable remotely Vendor: Mitsubishi Electric Equipment: Mitsubishi Electric, Multiple Factory Automation Engineering Software products Vulnerability: Permission Issues 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-212-02 Mitsubishi Electric Multiple Factory Automation Engineering Software Products that was…
Treck TCP/IP Stack
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely Vendor: Treck Inc. Equipment: TCP/IP Vulnerability: Heap-based Buffer Overflow, Out-of-bounds Read, Out-of-bounds Write The Treck TCP/IP stack may be known by other names such as Kasago TCP/IP, ELMIC, Net+ OS, Quadnet, GHNET v2, Kwiknet, or AMX. 2. RISK EVALUATION…
Emerson Rosemount X-STREAM
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Emerson Equipment: Rosemount X-STREAM Gas Analyzer Vulnerability: Improper Authentication 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker through a specially crafted URL to download files and obtain sensitive information. 3. TECHNICAL…
PTC Kepware KEPServerEX (Update A)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: PTC Equipment: Kepware KEPServerEX Vulnerabilities: Stack-based Buffer Overflow, Heap-based Buffer Overflow, Use After Free 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-352-02 PTC Kepware KEPServerEX that was published…
PTC Kepware LinkMaster
1. EXECUTIVE SUMMARY CVSS v3 9.3 ATTENTION: Low skill level to exploit Vendor: PTC Equipment: Kepware LinkMaster Vulnerability: Incorrect Default Permissions 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a local attacker to globally overwrite the service configuration to execute arbitrary code with NT SYSTEM privileges. 3….
Medtronic MyCareLink Smart
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable with adjacent access/low skill level to exploit Vendor: Medtronic Equipment: MyCareLink (MCL) Smart Model 25000 Patient Reader Vulnerabilities: Improper Authentication, Heap-based Buffer Overflow, Time-of-check Time-of-use Race Condition 2. RISK EVALUATION Successful exploitation of these vulnerabilities together could result in the attacker…









Stay connected