Hackers Breach Russian Bank and Steal $1 Million Due to Outdated Router
A notorious hacker group known as MoneyTaker has stolen roughly $1 million from a Russian bank after breaching its network via an outdated router. The victim of the hack is PIR Bank, which lost at least $920,000 in money it had stored in a corresponding…
Cisco fixes critical and high severity flaws in Policy Suite and SD-WAN products
Cisco has found over a dozen critical and high severity vulnerabilities in its Policy Suite, SD-WAN, WebEx and Nexus products. The tech giant has reported customers four critical vulnerabilities affecting the Policy Suite. The flaws tracked as CVE-2018-0374, CVE-2018-0375, CVE-2018-0376, and CVE-2018-0377 have been discovered during internal testing. Two of these flaws…
Russia’s national vulnerability database is a bit like the Soviet Union – sparse and slow
Russia’s vulnerability database is much thinner than its US or Chinese counterparts – but it does contain a surprisingly high percentage of security bugs exploited by its cyber-spies. Recorded Future’s Priscilla Moriuchi and Dr Bill Ladd found the database is highly focused yet incomplete, slow…
Passwords for Tens of Thousands of Dahua Devices Cached in IoT Search Engine
Login passwords for tens of thousands of Dahua devices have been cached inside search results returned by ZoomEye, a search engine for discovering Internet-connected devices (also called an IoT search engine). Discovered by Ankit Anubhav, Principal Researcher at NewSky Security, a cyber-security company specialized in…
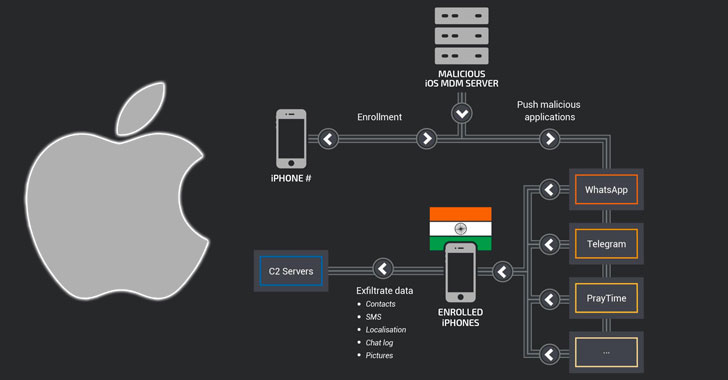
Hackers Used Malicious MDM Solution to Spy On ‘Highly Targeted’ iPhone Users
Security researchers have uncovered a “highly targeted” mobile malware campaign that has been operating since August 2015 and found spying on 13 selected iPhones in India. The attackers, who are also believed to be operating from India, were found abusing mobile device management (MDM)…
Hacker Sold Stolen U.S. Military Drone Documents On Dark Web For Just $200
You never know what you will find on the hidden Internet ‘Dark Web.’ It has been reported that a hacker was found selling sensitive US Air Force documents on the dark web for between $150 and $200. Cybercrime tracker Recorded Future today reported that…
Malicious Software Packages Found On Arch Linux User Repository
Yet another incident which showcases that you should not explicitly trust user-controlled software repositories. One of the most popular Linux distros Arch Linux has pulled as many as three user-maintained software repository AUR packages after it was found hosting malicious code. Arch Linux is an independently developed,…
Two New Spectre-Class CPU Flaws Discovered—Intel Pays $100K Bounty
Intel has paid out a $100,000 bug bounty for new processor vulnerabilities that are related to Spectre variant one (CVE-2017-5753). The new Spectre-class variants are tracked as Spectre 1.1 (CVE-2018-3693) and Spectre 1.2, of which Spectre 1.1 described as a bounds-check bypass store attack has…
Microsoft Releases Patch Updates for 53 Vulnerabilities In Its Software
It’s time to gear up your systems and software for the latest July 2018 Microsoft security patch updates. Microsoft today released security patch updates for 53 vulnerabilities, affecting Windows, Internet Explorer (IE), Edge, ChakraCore, .NET Framework, ASP.NET, PowerShell, Visual Studio, and Microsoft Office and…
Gaza Cybergang Returns With New Attacks On Palestinian Authority
Security researchers from Check Point Threat Intelligence Team have discovered the comeback of an APT (advanced persistent threat) surveillance group targeting institutions across the Middle East, specifically the Palestinian Authority. The attack, dubbed “Big Bang,” begins with a phishing email sent to targeted victims…









Stay connected