Siemens LOGO! (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: LOGO! Vulnerabilities: Insufficiently Protected Credentials, Man-in-the-Middle 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-17-243-02 Siemens LOGO! that was published August 31, 2017, on the ICS webpage…
Rockwell Automation FactoryTalk Linx
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/Low skill level to exploit Vendor: Rockwell Automation Equipment: FactoryTalk Linx Vulnerabilities: Improper Input Validation, Heap-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow a denial-of-service condition, remote code execution, or leak information that could be used…
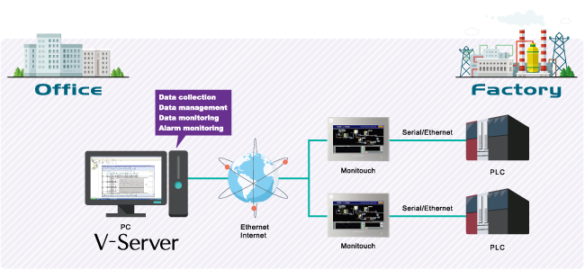
Fuji Electric V-Server Lite
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Fuji Electric Equipment: V-Server Lite Vulnerability: Out-of-bounds Write 2. RISK EVALUATION Successful exploitation of this vulnerability could allow for remote code execution on the device. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of V-Server…
Johnson Controls Sensormatic Electronics American Dynamics victor Web Client
1. EXECUTIVE SUMMARY CVSS v3 7.1 ATTENTION: Exploitable remotely Vendor: Sensormatic Electronics, LLC; a subsidiary of Johnson Controls Equipment: American Dynamics victor Web Client, Software House C•CURE Web Client Vulnerability: Improper Authorization 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an unauthenticated attacker on the network to…
Paradox IP150
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Paradox Equipment: IP150 Vulnerabilities: Stack-based Buffer Overflow, Classic Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to remotely execute arbitrary code, which may result in the termination of the…
Real Time Automation EtherNet/IP
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Real Time Automation (RTA) Equipment: 499ES EtherNet/IP (ENIP) Adaptor Source Code Vulnerability: Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability could cause a denial-of-service condition, and a buffer overflow may allow remote…
Schneider Electric Interactive Graphical SCADA System (IGSS)
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Schneider Electric Equipment: Interactive Graphical SCADA System (IGSS) Vulnerabilities: Improper Restriction of Operations within the Bounds of a Memory Buffer, Out-of-bounds Write, Out-of-bounds Read 2. RISK EVALUATION Successful exploitation of these vulnerabilities may result in remote…
BD Alaris 8015 PC Unit and BD Alaris Systems Manager
1. EXECUTIVE SUMMARY CVSS v3 6.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Becton, Dickinson and Company (BD) Equipment: BD Alaris 8015 PC Unit and BD Alaris Systems Manager Vulnerability: Improper Authentication 2. RISK EVALUATION Successful exploitation of this vulnerability could lead to a drop in the wireless…
Mitsubishi Electric MELSEC iQ-R Series
1. EXECUTIVE SUMMARY CVSS v3 6.8 ATTENTION: Exploitable remotely Vendor: Mitsubishi Electric Equipment: MELSEC iQ-R series Vulnerability: Uncontrolled Resource Consumption 2. RISK EVALUATION Successful exploitation of this vulnerability could cause a denial-of-service condition for the affected products. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Mitsubishi Electric reports the vulnerability affects…
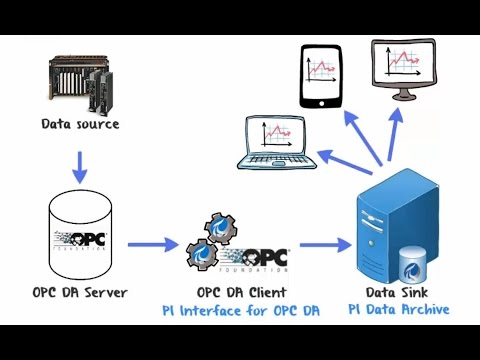
OSIsoft PI Interface for OPC XML-DA
1. EXECUTIVE SUMMARY CVSS v3 8.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: OSIsoft Equipment: PI Interface Vulnerability: Numeric Errors 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker-controlled OPC XML-DA Server to respond with a crafted XML message and exploit the PI Interface for…








Stay connected