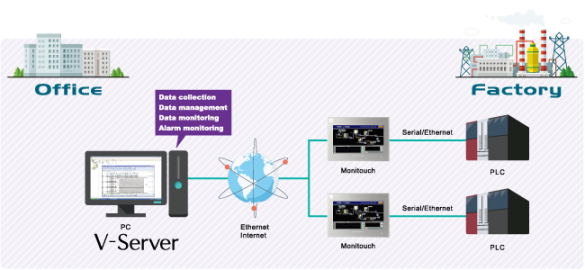
Fuji Electric V-Server
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Fuji Electric Equipment: V-Server Vulnerability: Heap-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability could crash the device being accessed; several heap-based buffer overflows have been identified. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The…
Philips Tasy EMR (Update A)
1. EXECUTIVE SUMMARY ——— Begin Update A Part 1 of 7 ——— CVSS v3 4.3 ATTENTION: Low skill level to exploit ——— End Update A Part 1 of 7 ——— Vendor: Philips Equipment: Tasy EMR ——— Begin Update A Part 2 of 7 ——— Vulnerability: Cross-site Scripting, Information Exposure…
Omron Network Configurator for DeviceNet (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.3 ATTENTION: Low skill level to exploit Vendor: Omron Equipment: Network Configurator for DeviceNet Vulnerability: Untrusted Search Path 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-19-134-01 Omron Network Configurator for DeviceNet that was published May 14, 2019,…
Interpeak IPnet TCP/IP Stack (Update C)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available Vendors: ENEA, Green Hills Software, ITRON, IP Infusion, Wind River Equipment: OSE by ENEA, INTEGRITY RTOS by Green Hills Software, ITRON, ZebOS by IP Infusion, and VxWorks by Wind River Vulnerabilities: Stack-based Buffer…
Omron CX-Supervisor
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Omron Equipment: CX-Supervisor Vulnerability: Use of Obsolete Function 2. RISK EVALUATION Successful exploitation of this vulnerability could result in information disclosure, total compromise of the system, and system unavailability. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS…
Honeywell equIP and Performance Series IP Cameras and Recorders
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely Vendor: Honeywell Equipment: equIP series and Performance series IP cameras and recorders Vulnerability: Authentication Bypass by Capture-Replay 2. RISK EVALUATION Successful exploitation of this vulnerability could result in unauthenticated access. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Honeywell reports the vulnerability…
Honeywell equIP and Performance Series IP Cameras
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Honeywell Equipment: equIP series and Performance series IP cameras Vulnerability: Missing Authentication for Critical Function 2. RISK EVALUATION Successful exploitation of this vulnerability could result in unauthenticated access. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Honeywell…
Honeywell equIP Series IP Cameras
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Honeywell Equipment: equIP series IP cameras Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could result in denial-of-service conditions. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Honeywell reports the vulnerability affects the…
Advantech WISE-PaaS/RMM
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Advantech Equipment: WISE-PaaS/RMM Vulnerabilities: Path Traversal, Missing Authorization, Improper Restriction of XML External Entity Reference, SQL Injection 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow information disclosure, remote code execution, and compromise system…
PHOENIX CONTACT Automation Worx Software Suite
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Phoenix Contact Equipment: Automation Worx Software Suite Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could compromise the availability, integrity, or confidentiality of an application programming workstation. Automated systems programmed using one…









Stay connected