Intel Data Center Manager SDK
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Intel Equipment: Data Center Manager SDK Vulnerabilities: Improper Authentication, Protection Mechanism Failure, Permission Issues, Key Management Errors, Insufficient Control Flow Management 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow escalation of privilege,…
Pangea Communications Internet FAX ATA
1. EXECUTIVE SUMMARY 1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available Vendor: Pangea Communications Equipment: Internet FAX Analog Telephone Adapter (ATA) Vulnerability: Authentication Bypass Using an Alternate Path or Channel 2. RISK EVALUATION Successful exploitation of this vulnerability could cause the…
Fuji Electric FRENIC Devices (Update A)
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available Vendor: Fuji Electric Equipment: FRENIC Loader, FRENIC-Mini (C1), FRENIC-Mini (C2), FRENIC-Eco, FRENIC-Multi, FRENIC-MEGA, FRENIC-Ace Vulnerabilities: Buffer Over-read, Out-of-bounds Read, Stack-based Buffer Overflow 2. UPDATE INFORMATION This updated advisory is…
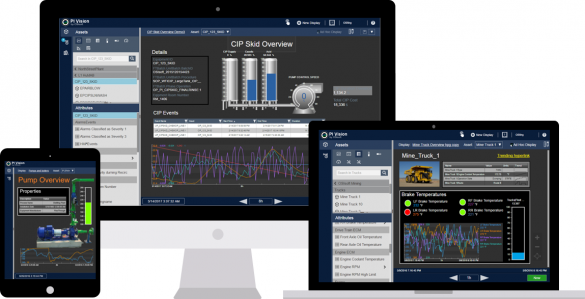
OSIsoft PI Vision
1. EXECUTIVE SUMMARY CVSS v4.8 ATTENTION: Low skill level to exploit Vendor: OSIsoft Equipment: PI Vision Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to read and modify the contents of the PI Vision web page and data related to the PI…
Siemens EN100 Ethernet Communication Module and SIPROTEC 5 Relays
. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: EN100 Ethernet Communication Module and SIPROTEC 5 Relays Vulnerability: Improper Input Validation 2. RISK EVALUATION The EN100 Ethernet communication module and SIPROTEC 5 relays are affected by a security vulnerability that could allow…
Siemens Licensing Software for SICAM 230
. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: WibuKey Digital Rights Management (DRM) used with SICAM 230 Vulnerabilities: Improper Input Validation 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow information disclosure, privilege escalation, or remote code execution. 3. TECHNICAL…
Siemens SIMATIC S7-300 CPU
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC S7-300 CPU Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could crash the device being accessed, resulting in a denial-of-service condition. 3. TECHNICAL DETAILS…
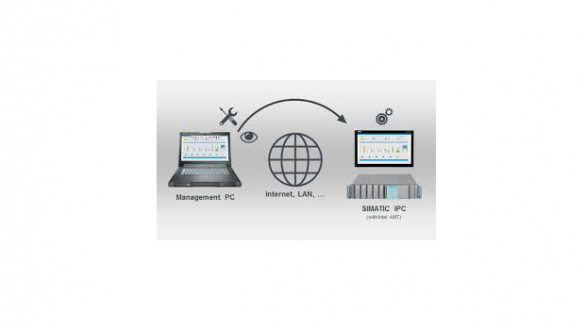
Siemens Intel Active Management Technology of SIMATIC IPCs
1. EXECUTIVE SUMMARY CVSS v3 6.7 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Intel Active Management Technology (AMT) of SIMATIC IPCs Vulnerabilities: Cryptographic Issues, Improper Restriction of Operations within the Bounds of a Memory Buffer, Resource Management Errors 2. RISK EVALUATION Successful exploitation of these vulnerabilities…
Siemens CP1604 and CP1616
1. EXECUTIVE SUMMARY CVSS v3 9.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: CP1604 and CP1616 Vulnerabilities: Cleartext Transmission of Sensitive Information, Cross-site Scripting, Cross-site Request Forgery 2. RISK EVALUATION Successful exploitation of these vulnerabilities could result in a denial-of-service condition and…
Privilege Escalation in Ubuntu Linux (dirty_sock exploit)
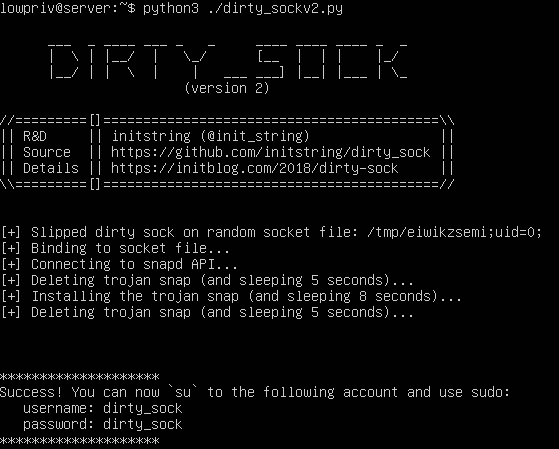
In January 2019, I discovered a privilege escalation vulnerability in default installations of Ubuntu Linux. This was due to a bug in the snapd API, a default service. Any local user could exploit this vulnerability to obtain immediate root access to the system. Two working…






Stay connected