Yokogawa iDefine, STARDOM, ASTPLANNER, and TriFellows
Legal Notice All information products included in http://ics-cert.us-cert.gov are provided “as is” for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information contained within. DHS does not endorse any commercial product or service, referenced in this product…
GE Intelligent Platforms Proficy HTML Help Vulnerabilities (Update A)
Legal Notice All information products included in http://ics-cert.us-cert.gov are provided “as is” for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information contained within. DHS does not endorse any commercial product or service, referenced in this product…
More Alerts Alert (TA18-201A) Emotet Malware
Overview Emotet is an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. Emotet continues to be among the most costly and destructive malware affecting state, local, tribal, and territorial (SLTT) governments, and the private and public sectors….
Predictive Analytics in Industrial IoT
The Industrial Internet of Things (IIoT) is a segment of Internet of Things (IoT) that’s often less visible than our common household objects such as cars, appliances, and central climate control that can be monitored and controlled by computers or smartphones. Dubbed the “fourth…
Hide And Seek malware – should I worry about the new IoT malware?
A malware infection is one of the worst things that could happen to your Internet of Things (IoT) devices. But some users don’t even know there are IoT-targeted attacks that threaten computers, networks, and data. Rebooting an IoT device is a simple way to remove…
You’re probably doing your IIoT implementation wrong
The Industrial Internet of Things promises a quantum leap forward in automation, centralized management and a wealth of new data and insight that is often too tempting to pass up. But automating a factory floor or a fleet of vehicles is far from simple, and…
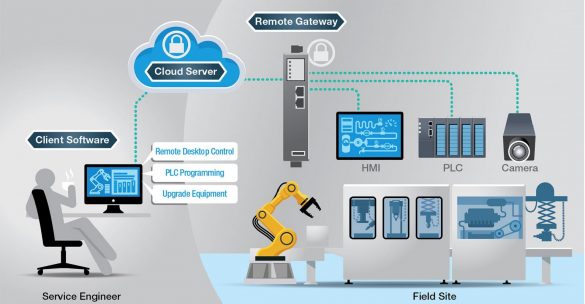
Five Issues Facing Secure Remote Access to IIoT Machines
The Industrial Internet of Things (IIoT) is changing the way business owners view their factories by giving them real-time data from machines and devices in the field that let them monitor and control production. Overall equipment effectiveness (OEE) and zero equipment downtime are no longer…
US CERT update on Home Network Security
What is home network security? Home network security refers to the protection of a network that connects devices to each other and to the internet within a home. Whether it’s staying in touch with friends and family, paying your bills electronically, or teleworking, the internet…
Top 10 IoT Security Tips
For most people, Internet of Things is, first of all, his home computer network of smart devices. The number of such devices and the need to connect them together and to the Internet is constantly increasing. Some devices work with local networks; others require access to…








Stay connected